Crawler
A web crawler, also known as a web spider or web robot, is a program, software package, or automated script which browses the Global Web in a systematic and automated method. Web crawlers are mostly used to generate a duplicate of all the pages they visit, then processing them throughout a search engine that will file the copied pages to deliver faster search results.
Credential Stuffing
Credential stuffing is a form of cyber-attack where a taken account's credentials, usually containing the lists of usernames and/or email ID along with the matching passwords, are stolen and then used to gain illegal access to real user accounts over a large-scale automated login.
Credentials
Credentials refer to achievements or titles bestowed upon someone, generally by an authoritative body, that are brought up in order to validate the capabilities and suitability of that person for a certain task.
Credit Bureau
A credit bureau is an organization that gathers and also investigates the entirity of credit information from a person and then sells the information to the creditors to get a fee so that they will able to make a decision regarding the permitting of a loan. These organizations usually associate with all kinds of loaning institutions and credit issuers to assist them in making any loan decisions.
Credit Card
A credit card is a thin four-sided block of plastic allotted by a financial firm that allows cardholders to borrow some funds to pay for products and services purchases. Credit cards are subject to the condition that cardholders must repay the borrowed cash, sometimes with interest or other charges.
Credit Card Fraud
Credit Card Fraud refers generally to any fraudulent transaction using a credit card as a source of funds. The fraudulent transaction may be committed to obtain goods or services or to illegally obtain funds from an account. Credit card fraud may occur simultaneously with identity theft, but can also occur when a legitimate consumer makes a purchase with no intention of paying for the goods or services, sometimes referred to as chargeback fraud or friendly fraud. Credit card fraud is related to debit card fraud, differing primarily in the form of payment. Another form of credit card fraud is new application fraud, in which a perpetrator applies for a credit card in a victim's name, then uses the card to purchase goods and services illegally. A victim’s credit card information can be acquired in a number of ways, by being purchased on the deep/dark web, by using skimmers at retail points of sale or ATMs, or through corporate data breaches.. The true cost of credit card fraud for merchants is more than just the cost of lost merchandise — it also includes lost profits, bank fees and chargeback costs.
Credit Card Fraud Detection
What is Credit Card Fraud Detection?
Credit card fraud detection refers to the set of policies, tools, methodologies, and practices that credit card companies and financial institutions use to prevent fraudulent purchases, both online and in-store. It involves using various techniques and technologies to identify potentially fraudulent transactions in real-time or post-transaction analysis. The goal is to minimize financial losses for both cardholders and card issuers by quickly identifying and stopping unauthorized or suspicious transactions.
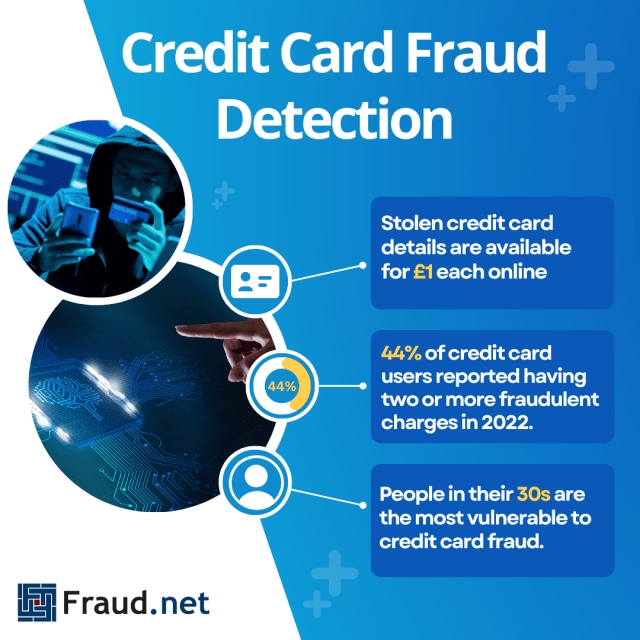
- Stolen credit card details are available for £1 each online
- 44% of credit card users reported having two or more fraudulent charges in 2022.
- People in their 30s are the most vulnerable to credit card fraud.
Common Types of Credit Card Fraud Detection
- Rule-Based Systems: These systems use predefined rules and thresholds to flag transactions that deviate from normal patterns. For example, if a card is used in multiple countries within a short time span, the system might flag it as suspicious.
- Machine Learning (ML) Models: ML algorithms can analyze historical transaction data to identify patterns associated with fraud. These models can learn from new data and adjust their detection techniques accordingly.
- Anomaly Detection: This approach involves identifying transactions that deviate significantly from the expected behavior. Anomalies might include large transactions, transactions in unusual locations, or transactions made at unusual times.
- Behavioral Analysis: This method focuses on understanding the typical spending behavior of a cardholder and flagging transactions that differ from that behavior.
- Geolocation Analysis: By analyzing the geographical location of a transaction and comparing it to the cardholder's usual locations, fraud detection systems can identify suspicious transactions.
How It's Different from Similar Fraud Detection
Credit card fraud detection has unique characteristics due to the nature of credit card transactions. Unlike other types of fraud detection, it:
- Focuses on financial transactions, especially electronic payments.
- Involves real-time monitoring to prevent immediate financial loss.
- Utilizes behavioral patterns and transaction history specific to individual cardholders.
- Needs to balance between minimizing false positives (legitimate transactions flagged as fraud) and false negatives (fraudulent transactions not detected).
It specifically focuses on preventing fraudulent purchases made using credit cards. It differs from other types of fraud detection, such as insurance fraud detection or healthcare fraud detection, which focuses on preventing fraudulent claims or transactions in those specific industries.
Solutions for Credit Card Fraud
Credit card fraud detection employs a multifaceted approach to safeguard financial transactions. Machine learning algorithms, including neural networks, decision trees, and ensemble methods, are adept at learning from historical transaction data to recognize fraud-related patterns. Predictive analytics harness historical data and statistical techniques to gauge the likelihood of a transaction being fraudulent. Real-time monitoring systems swiftly identify and thwart fraudulent activities as they unfold, ensuring prompt intervention.
Furthermore, biometric authentication offers an additional layer of security by utilizing traits like fingerprints and facial recognition, thereby mitigating the risk of unauthorized transactions. Behavioral analytics delves into spending habits, transaction frequencies, and behavioral trends to pinpoint irregular activities. Augmenting transaction data with external information, such as device data and geolocation, through data enrichment techniques, enhances the accuracy of fraud identification. This comprehensive arsenal of methods collaborates to fortify credit card fraud management, providing a dynamic defense against evolving fraudulent tactics.
For instance, a machine learning model trained on a dataset of legitimate and fraudulent transactions can learn to differentiate between normal spending patterns and unusual activities. Let's say a user typically makes transactions within a certain geographic region and at specific times of the day. If suddenly, there are multiple transactions from different countries or during unusual hours, the machine learning model can flag these transactions as potentially fraudulent.
Don't Wait for Fraud: Take Charge of Your Security Against Credit Card Scams!
Fraud.net offers a comprehensive fraud detection solution that combines machine learning algorithms, behavioral analytics, and real-time monitoring. It employs advanced algorithms to detect anomalies and suspicious behavior, helping businesses prevent credit card fraud. Request a demo today to learn more about how Fraud.net's solution can help your specific needs!
Credit Card Number
A credit card number is the exclusive number printed on a credit card. The first six numbers written on a credit card are the issuer's identification numbers, and the last remaining numbers are exclusive to the specific card. These credit card numbers are typically available in embossed form on the credit card.
Credit Card Refund Schemes
What are Credit Card Refund Schemes?
Credit card refund schemes are fraudulent activities in which scammers exploit the refund process of credit card transactions to illegitimately obtain money or goods. In refund schemes, fraudsters employ clever strategies to obtain money or items that they shouldn’t rightfully have. They engage in deceptive tactics to manipulate the way refunds are processed. This allows them to receive money that they have no legitimate claim to.
Credit card refund schemes can lead to financial losses for businesses, financial institutions, and individuals.
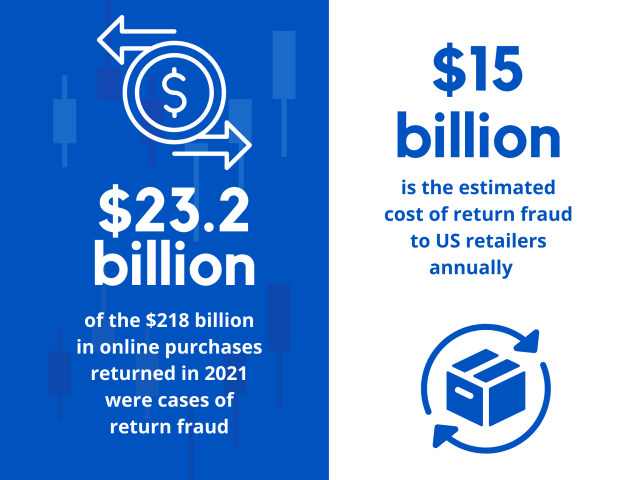
- Approximately $23.2 billion of the $218 billion in online purchases returned in 2021 were cases of return fraud
- Return fraud is estimated to cost US retailers over $15 billion in losses annually
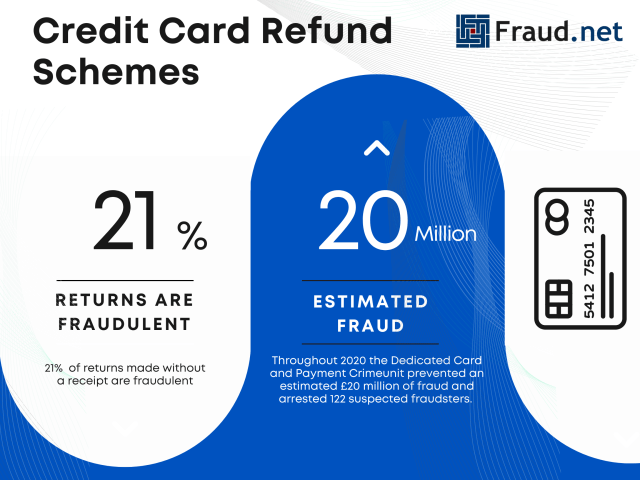
- 21% of returns made without a receipt are fraudulent
- The Dedicated Card and Payment Crime Unit protected an estimated £20 million from potential refund schemes and arrested 122 suspected fraudsters.
Common types of credit card refund schemes:
- Return Fraud: A fraudster purchases items using a credit card and then returns them for a refund, often claiming the items were defective or not received, even though they were never purchased.
- Overpayment Refund Fraud: The fraudster makes a larger payment than necessary and then requests a refund for the overpayment amount.
- Virtual Item Fraud: In online transactions, a fraudster may purchase virtual goods or services, claim they were never received, and request a refund.
- Collusion with Employees: Fraudsters collude with employees to process fake refunds and share the proceeds.
Credit card refund schemes differ from legitimate refund processes by involving deception or manipulation to obtain refunds that are not justified. Legitimate refunds are intended to rectify genuine errors or customer dissatisfaction.
Solutions for Refund Fraud
Mitigating credit card refund schemes involves a combination of strategies:
- Transaction Monitoring: Implement advanced analytics to detect patterns indicative of refund fraud, such as multiple refunds for the same item or excessive refund requests.
- Documentation Verification: Require detailed documentation for refund requests, including proof of purchase and reasons for the refund.
- Automated Fraud Detection: Utilize automated systems to cross-reference refund requests with historical transaction data and flag anomalies.
- Employee Training: Educate employees about common refund fraud tactics and how to identify suspicious refund requests.
- Refund Approval Process: Institute a multi-level approval process for refunds that involve high amounts or deviate from regular patterns.
- Customer Authentication: Implement strong customer authentication methods to verify the identity of the person requesting the refund.
- Data Sharing: Collaborate with industry partners and organizations to share information about known refund fraudsters and patterns.
Fraud.net’s Solution
Fraud.net offers an advanced fraud prevention solution with features tailored to combat credit card refund schemes:
Pattern Recognition, a crucial component, harnesses the capabilities of machine learning. By scrutinizing refund patterns and behaviors, this technology helps identify deviations that might suggest fraudulent activities. Transaction Analysis delves into historical transaction data. Its role is to meticulously sift through this data, aiming to uncover any irregularities or anomalies present within refund requests. This systematic examination contributes significantly to detecting suspicious activities and potential fraud.
Customer Verification stands as a pivotal safeguard in the refund ecosystem. It provides essential tools that enable organizations to verify the identities of their customers. This step is essential to ensure that refunds are direc
ted to the rightful recipients, preventing any illegitimate diversion of funds. The advantage of Real-time Monitoring cannot be overstated. It acts as a vigilant guardian, capable of issuing instant alerts when any suspicious refund activities are detected. This real-time notification system empowers organizations to intervene swiftly and prevent any further potential harm. Lastly, the importance of Industry Collaboration cannot be overlooked. A collective defense is established against evolving refund fraud tactics by fostering information sharing among different entities. This collaborative approach ensures that knowledge is pooled, enabling organizations to proactively adapt and counter emerging threats effectively.
We invite you to request a demo or consultation with our experts to explore how Fraud.net’s comprehensive fraud prevention solution can safeguard your business against credit card refund schemes and other fraudulent activities. Take proactive steps to protect your business’s financial integrity today.
Credit Fraud
Credit fraud is described as a situation where a customer's personal information has been stolen by a fraudster in order to make a new credit claim using the stolen information. In this case, the customer's name may not be authorized.
Cryptocurrency
A cryptocurrency is a virtual or digital currency that applies cryptography for safety purposes. A crypto currency is quite challenging to counterfeit because of the security feature. Many of the crypto currencies are distributed systems built on Blockchain technology, which is a scattered accounting book applied by a dissimilar system of computers.
Cryptogram
A cryptogram is a form of puzzle that contains a small part of encrypted text. Usually the code used to encrypt the text is quite simple so that the cryptogram can be resolved manually. Often the cryptogram is used for exchange codes where each letter is exchanged for a different number or letter.
Cryptography
Cryptography is the study (as well as the practice) of methods for secure communication in the presence of malicious third parties. Generally, cryptography is centered around creating and investigating procedures that prevent the public from reading confidential messages. A number of data security features such as data privacy, data truthfulness, verification, and even non-refutation are essential for contemporary cryptography.
Cryptomining
Cryptocurrencies require large amounts of computer power to be created, or “mined”. Some legitimate companies specialize in mass cryptomining through dedicated mining farms.
Cyber criminals and fraudsters, however, like to deploy cryptomining viruses or bots on unsuspecting users’ computers, or even organizations’ servers. This allows them to mine at scale, without spending extra money on equipment or resources like electricity.