Facebook is a social media or networking platform that uses the internet for its operation. It allows people to connect with others by creating an account and chatting with them over the internet. Facebook is supported by a variety of devices like mobiles, tablets, and personal computers.
Facial Recognition
Facial Recognition is a type of biometric check used to identify the person and unlock the system. It focuses on the facial structure of a person and identifies whether the person has the necessary authorization or not. Normally, it is used in phones and other security systems.
Fake check
A fake check is normally used by a fraudster with either a duplicate signature or writing for withdrawing cash from bank. This is a fairly common type of scam that is done by obtaining the necessary information from the real member of the bank to create a fake check and cash it later.
Fake merchandise
Fake merchandise includes products and services that are not authorized by the original company, but are sold with the name of the company. Fake merchandise is often used on the Internet through e-commerce websites where buyers cannot actually control the product.
False Account Entries
Fake Account Entries refer to the input of wrong or misleading information in terms of financial statements. It is ethically wrong to include fake account entries in software or in a book that has to be submitted to a financial manager.
False Data
False data refers to information which is not accurate, especially the information which, in a specific context, differs directly from the required information.
False Declines
False declines are generally referred to as false positives that occur when an actual transaction is apparently flagged by a protection system of a merchant and it is declined inadvertently. Often, it occurs when a cardholder trips into a merchant's fraud detection system.
False Documents
False documents are documents created with incorrect information that cannot be used for their required purposes because the document does not contain the necessary data. These documents are created for the purpose of deceiving others.
False Expense Claims
What are false expense claims?
Many organizations focus on external threats to fight fraud. However, internal threats can be just as devastating. Employees who feel entitled to something or who take advantage of lax policies can devise schemes to steal from your business. False expense claims are among the most common methods used.
Businesses have processes for reimbursing expenses that employees incur while on the job. These expenses can include travel costs, business lunches or supplies.
With false expense claims, staff - who are authorized to be reimbursed for a certain number of expenses incurred while carrying out their work duties - submit a claim for those reimbursements when they don’t actually deserve them. Essentially, they take advantage of this practice to submit reimbursement requests for expenses that aren’t legitimate.
This type of fraud can take on different forms:
- Fictitious expenses. Employees can use fake receipts or fill out blank receipts to claim they purchased something for work and get reimbursed. They can also submit a claim for trips they canceled.
- Overstated expenses. With overstated expense reports, employees claim they spent more than they actually did. They can, for instance, say they tipped more or fail to report that an item was discounted.
- Duplicate claims. It’s possible to use the same receipt or invoice more than once to submit multiple expense reports. This scheme can be hard to notice if your HR or accounting department is busy.
- Mischaracterized expenses. This scheme is one of the common types of false expense claims. Some mischaracterized expenses are legitimate errors because there are no clear policies for what the business will reimburse, but others are malicious claims from employees disguising personal purchases as business-related expenses.
How can false expense claims affect your business?
False expense claims are more common than you might think. After all, internal agents commit 37% of all fraud. Plus, 14.5% of all fraud is expense fraud. Indeed, it’s a costly issue since occupational fraud schemes cause $1.5 million in losses on average.
There are steps you can take to protect your organization from false expense reports, starting with reviewing your current policies for issuing reimbursements.
Stronger controls can make it harder to get past the employees who approve expenses. Having more than one employee involved, establishing who has the permission to issue a reimbursement, and escalating the request to a higher-level employee for claims above a certain amount can make it more difficult to submit false expense claims.
You should also go over your expense and reimbursement policies and update them. Create a list of allowable expenses and spending limits. Determine the reimbursement rate for mileage and list the documents employees will have to submit as proof. Review these rules regularly and adjust allowances to account for inflation.
Consider adopting company credit cards to oversee what employees spend instead of relying on receipts alone. You can also create a strong deterrent against internal fraud by implementing random audits of reimbursement requests.
Enforcing disciplinary measures if you find an employee to have submitted a false expense claim is another strong deterrent. Training can also increase awareness for this type of fraud and create a company culture where employees are more likely to report internal fraud.
False expense claims can be a costly issue. Besides, they can slow down the process of reimbursing legitimate business expenses. You can go further to save time and money by leveraging tech to create an additional layer of security.
How technology can help
You can build a more streamlined reimbursement process by doing away with paper receipts and adopting email to submit reimbursement requests. With Fraud.net’s Email AI tool, recipients will see a risk score for each email they receive and will know right away if a claim has been falsified.
Adopting our Transaction AI tool is another step you can take to protect your organization from false expense claims. This tool can detect fraudulent transactions by leveraging third-party APIs, our Collective Intelligence Network, and data from dynamic device fingerprinting to track users’ behaviors.
Don’t let false expense claims hurt your bottom line. Take action now and install Fraud.net's Email AI for free. And don't forget to take advantage of a free fraud analysis to create a stronger defense against all kinds of fraudulent activities.
False Expense Reimbursements
False Expense Reimbursements occur when an employee falsely inflates costs associated with their work, so that when they ask for reimbursements they will be given more money than they should.
False Financial Statements
False Financial Statements describe when a person falsifies income reports, balance sheets, and/or creates fake cash-flow statements to deceive the people who receive them. The purpose of this activity is generally personal profit.
False Front Merchants
False Front Merchants is when a company appears to have valid businesses, but actually, all are just fronts for a number of various fraud schemes. The ability of some fraudsters to make fake companies is growing with the new ways digital payment systems perform in a business, which give the opportunities for the fraudsters to set up sophisticated, deceptive schemes of false front merchants.
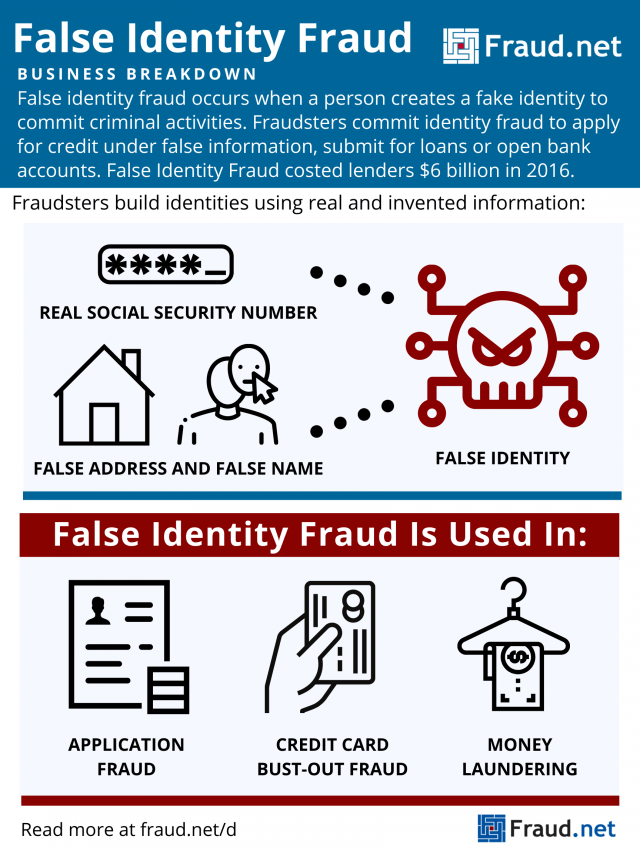
False Identity Fraud
What is False Identity Fraud?
False identity fraud occurs when a person creates a fake identity to commit criminal activities. Fraudsters commit identity fraud to apply for credit under false information, submit for loans or open bank accounts.
Fraudsters obtain the information they need to construct a false identity through identity theft methods like phishing, credit card fraud, and obtaining fullz. Once they have this information, they invent some of their own rather than impersonating a living person.
For example, they may combine an existing social security number with a falsified address and name. This results in a synthetic identity they then use to commit fraud. Additionally, they may engage in social engineering to make false identities seem more legitimate, to avoid detection.
Children’s SSNs are more likely to be selected for synthetic identity fraud, as they offer a blank slate for fraudsters to build their identity upon. Additionally, false identities can be harder to discover with childrens’ SSNs, as their financial history is rarely paid attention to until the child grows older. Unfortunately, children’s identity information is often easier to obtain due to their vulnerability to phishing and other online scams.
How Do Fraudsters Use False Identities?
Fraudsters use false identities to commit a variety of fraudulent and criminal actions. They include:
- Application Fraud – Fraudsters use the good reputation (or blank slate) of an identity to apply for loans or credit cards. Then, they disappear once it comes time to pay back the loan or credit debt. An application for a credit card, even if rejected, can serve to legitimize a false identity. Afterward, a fraudster can use that legitimated identity to apply for loans and credit cards more easily.
- Credit Bust-Out Fraud – Fraudsters open new credit accounts with falsified information and establish a normal usage pattern over several months or years. Suddenly, they max out all cards with no intention of paying back the debt. Then, they repeat the process.
- Money Laundering – Criminals use false identities to engage in the trafficking of people, money, and drugs. The use of false identities allows them to avoid government detection.
- Fraud Rings – Fraudsters manage thousands of fake accounts with falsified data to commit fraud simultaneously. In these, they employ methods like bust-outs or application fraud at a large scale.
The Cost to Businesses
False identity fraud accounted for about USD $6 billion in costs to lenders in 2016 and 20% of all credit losses for financial institutions that same year – and the number is only increasing. Aite Group discovered losses of USD $820 million to synthetic identity fraud in 2018. They project that number to increase to about USD $1.25 billion over the next two years.
However, the Federal Reserve presumes that the number could be much larger, due to particular fraud detection oversights, such as lack of investigation, lack of consistency in which attributes to assess, lack of awareness, and lack of reporting.
Fraud.net has a Solution
While attempting false identity fraud is considered a felony in most jurisdictions, the volume of attacks prompts organizations to prevent false identity fraud rather than prosecute it. They do so through methods of identity verification and rules-based screening. Additionally, they may do risk-scoring to approve or deny transactions based on how high of a potential fraud risk they are.
Artificial intelligence, data mining, and machine learning provide an edge to false identity fraud protection. Institutions protect their consumers better by stopping crime in its tracks rather than reacting after the fact.
Fraud.net combines AI & deep learning, collective intelligence, rules-based decision engines, and streaming analytics to detect fraud in real-time, at scale. To learn more about the solutions we offer to stop fraud before it affects your business, click “talk to a fraud expert” below.
False Invoices
False Invoices could be described as the situation where a person makes an invoice that does not relate to a real sale or payment and is used to get money dishonestly and undeservedly.
False Negative
A false negative is when a fraudulent transaction fails to be flagged as fraudulent, and gets through a system's fraud detection. It is the opposite of a false positive.
False Positive
False Positives, also known as “false declines” or “sales insults” appear when financial organizations or merchants decline valid orders. False positives are primarily caused by a businesses anti-fraud system incorrectly marking a transaction as likely to be fraud, when in truth the order is legitimate.
False Report
A false report is created when somebody knowingly reports a crime that did not occur, or knowingly reports details of a crime incorrectly.
False Reporting
False Reporting is when someone creates documents with false financial information and submits this information as legitimate.
False Sales Invoices
A contractor or supplier may commit fraud by knowingly submitting false, inflated or duplicated invoices with the intent to defraud the company they have been hired by. The contractor may act alone, or collude with payroll staff to keep the fraud going. The expression “false invoices” refers to invoices for goods or services that were never actually provided.
False Travel Claim
A false travel claim is when a person falsely claims they traveled by a certain method, and then asks to be reimbursed for paying for that method. An example would be if an employee said they had to take public transport to get somewhere, when in reality they simply walked or biked, and just want to make the money they say they spent.
False Vendors
False Vendors refer to any scheme that is completed by creating fake vendors. This can have multiple uses for fraud; for one, the fraudster can send invoices to companies asking for payments on a service or good that was never actually provided. Another example is when a fraudster will create a duplicate payment system, causing consumers to have to pay twice to buy a good, one payment going to the fraudster.
Falsified Hours
Falsified Hours is the term for when an employee records themselves as having worked more hours than they truly have in order to be paid for work they have not done.
Familiar Fraud
Familiar fraud describes when a customer asks for a chargeback instead of pursuing a refund from the merchant they made the purchase with, with the purpose of keeping their funds while also getting the product they bought.
Federated Identity
A federated identity in information technology refers to process of linking a person's electronic identity and attributes across multiple distinct identity management systems. Federated identity is related to single sign-on (SSO), in which a user's single authentication ticket or token, is trusted across multiple IT systems or even organizations. SSO is a subset of federated identity management, as it relates only to authentication and is understood on the level of technical interoperability and it would not be possible without some sort of federation.
Fictitious Refunds
In a fictitious refund scheme, an employee processes a transaction as if a customer were returning merchandise, even though there is no actual return. Since the transaction is fictitious, no merchandise is actually returned. The result is that the company's inventory is overstated.
FIDO
Fast Identity Online is a set of open technical specifications for mechanisms of authenticating users to online services that do not depend on passwords. FIDO authentication seeks to use the native security capabilities of the user device to enable strong user authentication and reduce the reliance on passwords.
Financial Crime
Financial Crime is a category of crime that is performed against property, comprising of the illegal conversion of the property rights to the personal use and benefits of the fraudster. Financial crime may involve fraud types such as securities fraud, credit card fraud, bank fraud, and more.
Fingerprint Recognition
Fingerprint Recognition is one of the most popularly used biometrics, and so far it is considered the most secure authentication method. Fingerprint Recognition refers to the automatic process of identifying or approving the identity of a person built on the comparison of two fingerprints.
Fintech Fraud
Fintech fraud refers to any fraud that takes place that is related to fintech in some way. Fintech fraud scandals can involve peer-to-peer financing platforms as well as crowd funding platforms, and have served as stark reminders of the risks from the use of Fintech where the proper rules or regulations on transactions are not present.
Firewall
A firewall is a system designed to prevent unauthorized access to or from a private network. You can implement a firewall in either hardware or software form, or a combination of both. Firewalls prevent unauthorized internet users from accessing private networks connected to the internet, especially intranets.
Food Fraud
Food fraud is the activity of changing, perverting, mislabeling, replacing or interfering with any food product at any theme alongside the farm–to–table food supply–chain. The fraud may appear within the fresh material, inside the ingredient, in the finishing product or maybe in the wrapping or packaging of the food.
Forged Signatures
Forged signatures are signatures created to look like very similar or the same as another's signature, but that was not created/signed by the signature's original creator. This is done to provide false authentication on documents; for example, a fraudster could "forge" a signature on a check to take money from someone without permission.
Fortune Teller Scam
Fortune teller scam, also known as the “bujo”, is a type of confidence game. The basic feature of the scam involves diagnosing the victim (the "mark") with some sort of secret problem that only the grifter can detect or diagnose, and then charging the mark for ineffectual treatments.
Fraud
Fraud is defined generally as the wrongful or criminal act to deceive someone for one's own financial or personal gain. Legal definitions of fraud vary across countries, at the federal and state levels in the US, and even among states, but most have, at their core, the use of deception to make a gain by unlawful or unfair means. Many types of fraud exist, including occupational, operational, investor, accounting, credit card and insurance fraud, but all forms share the fact that the perpetrator knowingly receives a benefit to which they're not rightfully entitled. The purpose of fraud may be financial gain but also covers the acquisition of other benefits, such as obtaining a driver's license, a passport or other travel documents, or qualifying for a mortgage by using falsified documents or making false statements.
Fraud
Fraud can be described as a consciously dishonest and/or illegal act done generally for personal gain, or to afflict another. Fraud can violate civil law, and cause the loss of cash, property, or other legal rights.
Fraud Analyst
A fraud analyst is someone who investigates forgery and theft within customers' accounts and transactions on behalf of a bank or a financial institution. They track and monitor the bank's transactions and activity that comes through the customers' accounts.
Fraud Department
Insurance corporations, banks, shops, and a mass of other companies employ fraud analysts to identify and prevent fraudulent activities, and if an organization dedicates a group of their employees to this task, they are known as a company's "fraud department".
Fraud Detection
Fraud detection is a set of activities undertaken to prevent money or property from being obtained through false pretenses. Fraud detection is applied to many industries such as banking or insurance. In banking, fraud may include forging checks or using stolen credit cards.
Fraud Examiner
A fraud examiner is a highly qualified professional who investigates cases of criminal and civil fraud. Fraud examiners can be certified to prove their expertise within the field of fraud and fraud prevention.
Fraud Filter: Understanding an Essential Tool for Transaction Security
Losses to online payment fraud are continually increasing, expected to grow from 41 billion US to 48 Billion USD in 2023 and increase by 131% over the next five years. With smart devices becoming increasingly available to most consumers and online activity increasing, transactions are more vulnerable than ever, with more vectors for fraud attacks.
Fraudsters can cause significant damage to businesses and customers by exploiting security vulnerabilities, leading to financial losses and reputational damage. Fortunately, tools are available to help prevent fraud, such as fraud filters.
What is a fraud filter?
A fraud filter is a tool to prevent fraudulent transactions from being processed. Fraud filters use a combination of algorithms and rules to analyze various data points related to a transaction, such as IP address, device information, shipping and billing address, and more. These data points are evaluated against known fraud patterns and stolen credentials, helping identify fraudulent activity.
Some common ways companies use fraud filters include:
- Analyzing transaction patterns: Fraud filters can flag transactions that appear unusual compared to a customer’s regular spending habits. For example, if a customer starts making much larger or more frequent purchases, a filter may flag this as potentially fraudulent.
- Monitoring suspicious account activity: Banks and fintechs may use filters to alert their fraud and risk team of unusual account behavior, such as multiple failed login attempts or several large money transfers.
- Machine learning: Filters can help financial institutions analyze transaction data, identify fraud patterns, and learn from past fraud cases to adjust their rules.
- Real-time risk assessment: Banks can rapidly risk assess incoming transactions for their likelihood of fraud. A filter may cancel the transaction or flag it for manual review if the risk meets a certain threshold.
As a result, businesses reduce their risk of financial losses and reputational damage caused by fraudulent activities while ensuring a secure experience for their legitimate customers. And they can avoid friction for legitimate customers while filtering out bad actors.
What types of companies typically use fraud filters?
Any business that accepts online payments and processes transactions through its website can benefit from a fraud filter, from banks and fintechs to businesses that sell physical goods, digital products, or services. More specifically, banks, fintechs, payment providers, and similar financial institutions process a high volume of transactions and are often targeted by fraud – so, they benefit a great deal from tools like fraud filters.
With financial fraud schemes increasing and online spending skyrocketing, having a robust fraud prevention strategy is more important than ever.
How does Fraud.net use fraud filters?
Fraud.net’s platform uses advanced machine learning algorithms and rules-based analytics to identify potentially fraudulent activity and analyze a wide range of data points related to a transaction to identify patterns of fraudulent behavior and can flag potentially fraudulent transactions.
By leveraging millions of data points and the industry’s leading solution providers, Fraud.net’s machine learning algorithms can quickly and accurately risk score transactions in less than a second for fraud teams to easily make decisions on. And their machine learning engine learns from each approved or denied transaction in future risk scoring of a particular event.
Suppose a transaction is flagged as potentially fraudulent by the fraud filter. In that case, Fraud.net offers a range of additional tools and services to help businesses investigate and resolve the issue, including real-time alerts, case management workflows, and access to a global network of fraud experts who can provide additional support and insights. Our company also offers an auto-cancel feature for transactions that trigger volume or location rules and risk score thresholds.
As a result of using our fraud filtering platform, customers have enjoyed an increased ROI, reduced time to review, reduced false positives, and, most of all, protected profits. To learn how Fraud.net’s tools can help you achieve the same, schedule a free demo with our solutions consultants today.
Fraud Guidelines
Fraud Guidelines are the practical guidelines put in place to help prevent, detect, and investigate any type of fraud that may occur within a business's dealings.
Fraud Jobs
Fraud jobs are the category of jobs that work in the fraud field, such as a fraud specialist, forensic accountant, forensic audit manager, forensic director, senior auditor, risk assurance and risk analyst, audit consultant, forensic service manager or a forensic auditor.
Fraud Lawyers
Fraud Lawyers are lawyers who practice law in the criminal fraud and civil areas. These lawyers assist companies who have been affected by fraud performed by their employees or other party by performing internal investigations, collecting proof, and communicating with the authorities as well.
Fraud Managed Services
Fraud Management Services are defined as the associations that provide support in reviewing and resolving all potential fraudulent operations of a company, assisting the company in the immediate cancellation and then refunding of illicit purchases. These associations conduct ongoing anti-fraud investigations to create innovative fraudulent policies to increase controls.
Fraud Prevention
What is Fraud Prevention?
Fraud Prevention refers to the strategies, measures, and systems put in place to detect and mitigate fraudulent activities or behaviors aimed at deceiving or stealing from individuals, organizations, or systems. It can take various forms, such as identity theft, credit card fraud, insurance fraud, and more. Fraud prevention aims to reduce the occurrence of fraud and minimize its impact when it does happen.
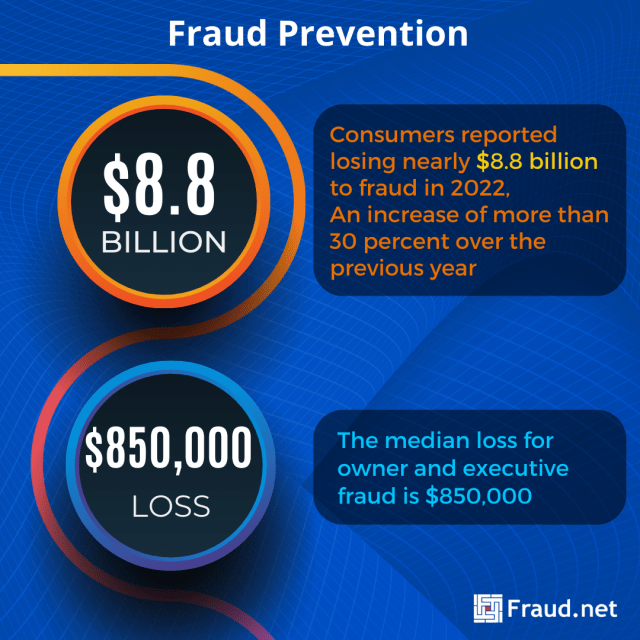
Some major losses and statistics around fraud include:
- The typical organization loses 5% of its revenue to fraud each year, according to the Association of Certified Fraud Examiners (ACFE). Applied to the estimated 2022 Gross World Product, which is 95 Trillion, this figure translates to a potential fraud loss of more than $4.75 trillion.
- The median loss for owner and executive fraud is $850,000.
- Newly released FTC data shows that consumers reported losing nearly $8.8 billion to fraud in 2022, an increase of more than 30 percent over the previous year.
Common Types of Fraud Prevention
The most frequently used methods of fraud prevention include:
- Identity Verification: Verifying the identity of individuals or entities using various methods. For example, document verification, biometrics, and knowledge-based authentication.
- Transaction Monitoring: Real-time monitoring of financial transactions to detect anomalies or suspicious patterns, such as unusually large transactions or multiple transactions from different locations.
- Machine Learning and AI: Utilizing machine learning algorithms and artificial intelligence to analyze vast amounts of data and identify fraudulent patterns and trends that may not be apparent to human analysts.
- Data Analytics: Analyzing historical data to identify trends and patterns associated with fraudulent activities, helping organizations make informed decisions about fraud prevention.
- Multi-factor Authentication (MFA): Requiring users to provide multiple forms of authentication, such as passwords, biometrics, and one-time codes, to access sensitive information or perform transactions.
- Geolocation and IP Tracking: Tracking the physical location of devices and users to detect suspicious logins or transactions from unexpected locations.
- Behavioral Analysis: Analyzing user behavior and comparing it to known patterns to detect anomalies that may indicate fraudulent activity.
- Educating Customers: about common fraud schemes and warning signs to help them avoid falling victim to scams.
How It Differs from Other Security Measures
- Cybersecurity: While fraud prevention includes aspects of cybersecurity, it specifically focuses on preventing financial losses due to fraudulent activities. Cybersecurity encompasses a broader range of threats, including data breaches and cyberattacks.
- Risk Management: Fraud prevention is a subset of risk management. It specifically focuses on mitigating financial and reputational risks associated with fraudulent activities.
Bolster Your Prevention With These Solutions
Most prevention tools are rules-based, but you can achieve more comprehensive risk management by adding a number of tools to your arsenal. These technologies make fraud prevention systems more accurate and provide end-to-end fraud and money laundering monitoring.
- AI and Machine Learning Tools: Employ machine learning models to analyze data in real-time and identify fraudulent transactions or behaviors.
- Identity Verification Services: Use third-party services to verify customer identities through document checks, biometrics, and identity databases.
- Analytics Platforms: Invest in software platforms that provide comprehensive fraud detection and prevention capabilities. These are often powered by AI and machine learning.
- Awareness Training: Train employees and customers to recognize fraud attempts and respond appropriately.
- Compliance and Regulatory Tools: Ensure adherence to industry regulations and compliance standards to prevent fraudulent activities.
Comprehensive Fraud Monitoring with Fraud.net
Fraud.net offers a comprehensive fraud prevention solution powered by advanced AI and machine learning. Our solution includes:
- An all-encompassing fraud prevention solution driven by cutting-edge AI and machine learning technology. Our AI-powered platform perpetually monitors transactions and user interactions to swiftly identify and thwart fraudulent activities.
- Robust identity verification services to validate the authenticity of both users and entities. Moreover, our platform meticulously scrutinizes transaction data. It swiftly pinpoints suspicious patterns and initiates immediate preventive actions to counter fraud effectively.
Request a demo today to learn more about how Fraud.net’s solution can protect your business from fraud. Take the next step in safeguarding your organization’s financial well-being and reputation with Fraud.net’s advanced fraud prevention tools.
Fraud Prevention Software
A number of merchants incorporate fraud protection software within their loss-prevention approaches. These automatic software programs support the companies to identify hazardous transactions in real time and decrease the amount of consumer fraud that occurs. Through an algorithm, the fraud protection software scans transactions, and uses previous transactional facts to uncover any potential risks and then marks the transactions to be further investigated.
Fraud Prevention Specialist
A Fraud Prevention Specialist is a person in a company who has the responsibility of taking care of certain assets and ensuring they remain protected from any potentially fraudulent actions. Their goal is both to detect any fraud occurring and then to also stop it.
Fraud Response Plan
A Fraud Response Plan is a policy aimed at ensuring that effective and timely action is taken in the event of fraud occurring. A Fraud Response Plan gives employees the details of the entire procedure for reporting any suspected fraud, defines the actions that the company needs to take and also defines authority levels, responsibilities for action, and reporting lines in the event of a suspected fraud or irregularity.
Fraud Ring
Fraud Ring
A Fraud Ring could be described as an organization which performs activities with the intention to defraud or take advantage of other people. This organization might be involved in any kind of forgery. Actions can range from creating fake claims, stealing a private identity, or even counterfeiting checks and currency. Some rings are devoted to committing fraud against ecommerce websites. Others are devoted to defrauding charities, businesses or government agencies. These organizations can consist of 10 criminals or 10,000. Most are devoted to committing specific types of fraud.
With the rise of the internet, online fraud is rampant. Millions of consumers are filling out online forms that require them to submit personal information, including as credit card numbers, SSIDs, street addresses, etc. Consequently, identity theft is the most popular type of Internet fraud.
Methods Used by Fraud Rings
There are many known cases of organizations that have carried out insurance fraud. For example, in 2017 a small scale ring of 26 individuals was prosecuted for staging traffic accidents to file false claims. This smaller group collected more than $100,000 in payouts from 12 auto insurance providers.
Payouts can be much larger. In 2012, a federal court in Minneapolis sentenced a California man and a New York man for their roles in a $50-million bank fraud conspiracy that operated in six states. This gargantuan scheme involved a network of bank employees and victimized more than 500 individuals around the world by stealing their personal and financial information. Bank fraud rings like this one may steal large quantities of checks and forge signatures. They may complete false loan applications or use stolen credit card numbers. Additionally, identity thieves steal personal information to apply for bank accounts or debit cards.
Protection Against Organized Fraud
The Association of Certified Fraud Examiners estimates that total global fraud losses total nearly $5 trillion, and fraud rings are a large part of this. A large group working towards organized fraud can do more financial damage than any individual fraudster ever will. The more individuals added, the more complex the issue becomes.
With that said, complex problems require sophisticated solutions. Many companies thus integrate a digital risk management platform into their workflow to combat fraud at minimal costs. This enables your company to extract immediate value and gain transparency, confidence, and clarity. Make the effort to prevent this type of fraud from affecting your business.
Learn More
Contact us for a demo and recommendations for fraud prevention and identity protection.
Fraud Risk Assessment
A fraud risk assessment is a tool used by business management to identify and understand risks to their business and weaknesses in controls that present a fraud risk to the organization. Once a risk is identified, a plan can be developed to mitigate those risks by instituting controls or procedures and assigning individuals to monitor and effectuate the plan of mitigation.
Fraud Risk Profile
There are two types of Fraud Risk Profiles: that of employees who abuse company assets to obtain personal benefits, and that of people who create the fraud plan in order to give the impression that will make the company look more profitable than it really is.
Fraud Schemes
Fraud Schemes are schemes that fraudsters have created to execute a criminal or fraudulent scenario, in order to obtain the personal benefits derived from it. Corruption, money laundering, skimming cash, and more are all fraud schemes.
Fraud Score
Fraud Score
A Fraud Score is an informational tool that helps you gauge risk involved with orders before processing. This is done by identifying traits and historical trends associated with suspicious behavior and fraudulent orders. This process is commonly used across businesses, as they try to detect fraud in their transactions to avoid major profit losses. Fraud detection is applied to many industries like banking, insurance, and e-commerce. With so much at stake and so many variables changing, it’s vital to have a real-time monitoring system for fraud.
The Score Model
At Fraud.net, we build custom machine learning models, leveraging patent-pending methodologies. In other words, we are determined to solve the unique and nuanced problems of each client, and develop a unique fraud score for each transaction.
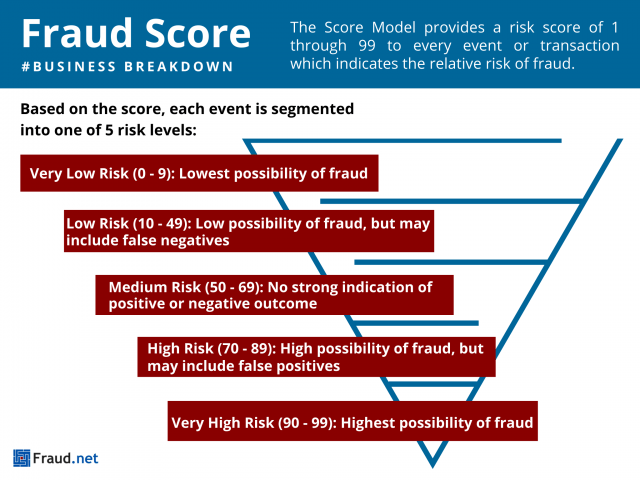
- The Score Model provides a risk score of 1-99 to every event or transaction. In short, this score indicates the relative risk of fraud.
- Based on the score, each event is segmented into one of 5 risk levels:
- Very Low Risk (0 – 9): Lowest possibility of fraud.
- Low Risk (10 – 49): Low possibility of fraud, but may include false negatives (risk).
- Medium Risk (50 – 69): No strong indication of positive or negative outcome.
- High Risk (70 – 89): High possibility of fraud, but may include false positives.
- Very High Risk (90 – 99): Highest possibility of fraud.
Using this method, clients are able to prioritize reviews of transactions based on risk. Thus, businesses can take real action based on risk group to reduce queue size and optimize investigator or review agents’ time.
Assess Risks Quickly and Efficiently
Deep in the terabytes of data your organization produces every day lie hidden, potentially game-changing, insights.
Using modern technology, unifying data and extracting intelligence is now possible. Consequently, assessing risks and saving businesses money has never been easier with the rise of AI.
Above all else, making sure your business is protected at all times is paramount.
Contact Fraud.net to schedule a demo of our end-to-end anti-fraud prevention system or a free fraud analysis. Start mitigating insider fraud risks today.
Fraud Screening
Fraud Screening generally refers to a checking system that identifies potentially fraudulent transactions. Fraud screening helps reduce fraudulent credit card transactions, reduce the number of manual reviews, minimizes risky sales, and improves a company’s bottom line.
Fraud Statistics
Fraud Statistics are reports produced by companies and organizations that detail things like the numbers of fraudulent transactions that have occurred in a period, what kinds of fraud took place, and anything else related to data on fraud. These fraud statistics are used to figure out how much and what kind of fraud occurs, so that a better preventative plan can be created to mitigate the impacts of fraud.
Fraud Triangle
The Fraud Triangle is a simple framework that is useful to understand a worker's decision to commit workplace or occupational fraud. The fraud triangle consists of three components (sides) which, together, lead to the workplace fraud, and are: 1) a financial need, 2) a perceived opportunity, and 3) a way to rationalize the fraud as not being inconsistent with their own values. The Fraud Triangle is a common teaching aide and metaphor that has been used for decades.
Fraud Upon The Court
Fraud on the court occurs when the judicial machinery itself has been tainted, such as when an attorney, who is an officer of the court, is involved in the perpetration of a fraud or makes material misrepresentations to the court. Fraud upon the court makes void the orders and judgments of that court.
Fraud vs Abuse
What is Fraud vs. Abuse?
Fraud and abuse are related concepts often used in the context of unethical or illegal activities, but they have distinct meanings.
Fraud: Fraud involves intentional deception or misrepresentation to gain an unfair or dishonest advantage. It often involves deceit, manipulation, or false information to obtain financial or personal benefits. Examples include credit card fraud, identity theft, insurance fraud, and Ponzi schemes.
Abuse: Abuse refers to the misuse or excessive use of something in a way that is harmful or goes beyond its intended purpose. In the digital realm, abuse often refers to misusing systems, services, or platforms. Examples include email spamming, click fraud, and the use of bots to manipulate social media engagement.
Here are some more recent statistics related to fraud and abuse: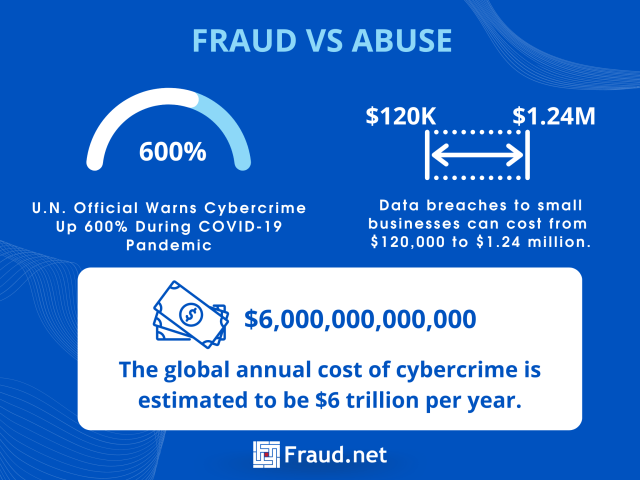
- The global annual cost of cybercrime is estimated to be $6 trillion annually.
- According to the UN, cybercrime rose 600% during the COVID-19 pandemic.
- The average cost of a data breach to small businesses can range from $120,000 to $1.24 million.
Common Fraud Schemes vs Common Abuse Tactics
Some of the most common types of fraud include:
- Account Takeover: Unauthorized individuals gain access to user accounts, often through phishing or hacking, and exploit them for financial gain or to impersonate the account holder.
- Application Fraud: Fraudsters provide false information or documents when applying for services, credit, or accounts, with the intent of securing benefits dishonestly.
- Business Email Compromise (BEC): Cybercriminals compromise business email accounts to conduct scams, including invoice fraud, which trick organizations into making payments to fraudulent accounts.
- Collusion: Multiple individuals work together, often within an organization, to manipulate systems, transactions, or data for illegal gain.
- Insider Threats: Individuals with authorized access to systems and data misuse their privileges for personal gain, often involving theft of sensitive information or fraud against their own organization.
On the other hand, some of the most common types of abuse include:
- Email Spam: Sending unsolicited and often irrelevant emails to many recipients.
- Click Fraud: Intentionally clicking on online ads to generate revenue or exhaust an advertiser’s budget.
- Social Media Manipulation: Using bots or fake accounts to inflate likes, shares, and comments on social media posts.
- Content Scraping: Unauthorized copying of online content for commercial gain.
- API Abuse: Misusing application programming interfaces (APIs) to overwhelm servers or access unauthorized data.
Differences between Fraud vs. Abuse
Fraud is centered around intentional deception for personal gain, often involving financial harm. On the other hand, abuse can be intentional or unintentional and may involve misuse or overuse of resources or systems without necessarily gaining direct economic benefits. Both can have negative impacts on individuals and businesses.
Solutions for Fraud vs. Abuse
Effective solutions for preventing and mitigating fraud and abuse often involve a combination of technological tools, process improvements, and user education. Here are some general strategies:
- In the realm of cybersecurity, a multifaceted approach is essential to safeguard sensitive systems and information. Employing advanced data analytics forms a formidable shield against potential threats. By meticulously scrutinizing data, one can uncover subtle anomalies and behaviors that often signal the presence of fraud or abuse, enabling swift and effective countermeasures.
- User protection extends further with the strategic implementation of multi-factor authentication and identity verification. This preventive measure is a robust barrier, deterring unauthorized access and fortifying security layers. Leveraging the power of machine learning and AI bolsters defenses even further. Through continuously analyzing evolving tactics, these algorithms adeptly discern and adapt to novel fraudulent or abusive activities, maintaining an unwavering vigilance against threats.
- To ensure a resilient security ecosystem, consistent monitoring and auditing are paramount. Regular assessments allow companies to proactively detect and address suspicious activities, nipping potential breaches. Moreover, empowering users with knowledge is the backbone of a good defense strategy. Educating individuals about prevalent fraudulent and abusive tactics empowers them to recognize and thwart potential threats, creating a united front against cyber adversaries.
Fraud.net’s Solution
Fraud.net offers an AI-driven fraud prevention platform that addresses fraud and abuse challenges. Our solution includes:
- Advanced Analytics and machine learning to identify fraudulent patterns and abusive behaviors.
- Real–time Monitoring of transactions and account activities to detect anomalies.
- Customizable Rules and thresholds to flag suspicious activities based on specific criteria.
- Behavioral Biometrics to analyze user behavior for authentication and fraud detection.
- Case Management tools, allowing teams to investigate and resolve flagged incidents.
Ready to protect your business from fraud and abuse? Book a demo with Fraud.net today to see how our advanced AI-powered solution can safeguard your operations. Request a demo now and ensure the security of your digital environment.
Fraud vs Forgery
In today’s world, the rapid development of technology can make it difficult to fight fraud and forgery, especially for legal authorities. Knowing what charges come with each, and primarily how to prevent them, is vital to saving your business significant costs per year.
Essentially, Fraud denotes any kind of practice of dishonesty of a person or a company for financial advantage. It is generally considered a well-thought-out crime by the law. On the other hand, forgery is essentially concerned with a produced or altered object. Fraud is the crime of deceiving another, which may be performed through the use of objects obtained through forgery. Forgery is a common technique in fraud schemes, where the fraudster uses forged documents in order to gain access to information or materials they should not truly have access to. The legalities and sentencing for each is extremely nuanced, but can provide insights for your business on which steps to take to both prevent and combat existing fraud.
Acts of fraud can be legally classified up to a Class I Felony , with fines up to $10,000 and a prison sentence of up to 3.5 years, and is an overarching term for many different federal charges. The average imprisonment time for counterfeiting (or forgery) is roughly 16 months.
Contact Fraud.net to schedule a demo of our end-to-end anti-fraud prevention system or a free fraud analysis, and start mitigating both forgery and fraud risks today.
Fraud vs Theft
Understanding Fraud and Theft: Key Differences, Types, and Preventive Solutions
Fraud and theft are both deceptive practices that involve unlawfully acquiring someone else’s assets, but they differ significantly in their execution and impact. Understanding these differences is crucial for businesses and individuals alike to protect themselves from financial losses and damage to their reputations. In this article, we will explore the disparities between fraud and theft, the common types of each, and preventive solutions to safeguard against these malicious acts.
Here are some statistics related to fraud and theft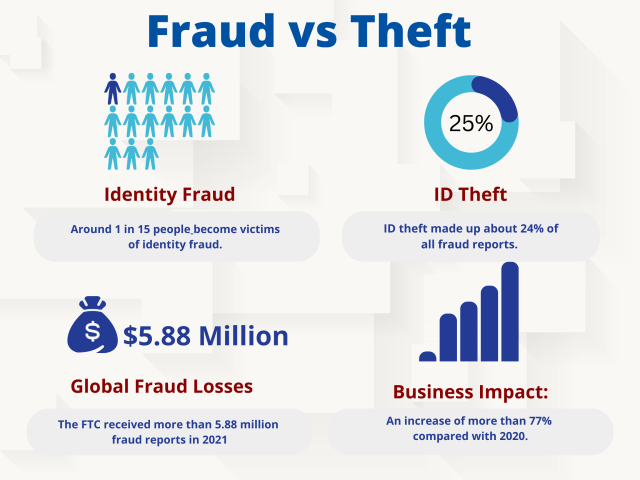 :
:
- Around 1 in 15 people become victims of identity fraud.
- In 2021, identity theft complaints topped the list of fraud reports received by the FTC, with 1,434,695 complaints. ID theft made up about 24% of all fraud reports.
- The FTC received more than 5.88 million fraud reports in 2021, a 19% increase from the year prior. Reports of associated financial losses topped $6.1 billion, an increase of more than 77% compared with 2020.
These statistics highlight the prevalence of fraud and theft in various forms, including identity theft, employee theft, and credit card fraud. It is important for individuals and businesses to take steps to protect themselves from these types of crimes, such as using strong passwords, monitoring financial accounts regularly, and implementing security measures like two-factor authentication.
Fraud vs. Theft: Key Differences
Fraud and theft are distinct in their approach and intent. Theft is a straightforward act of taking someone else’s property or belongings without their permission, intending to permanently deprive them of it. In contrast, fraud involves deceptive practices or misrepresentation with the intent to gain something of value, such as money or goods, through dishonest means. In essence, while theft involves physical or direct possession of assets, fraud relies on cunning manipulation or deception to achieve its objectives.
Common Types of Fraud and Theft
Fraud encompasses various types, including identity theft, credit card fraud, insurance fraud, and online scams. Identity theft occurs when a criminal steals personal information to commit financial fraud in the victim’s name. Credit card fraud involves the unauthorized use of someone’s credit card to make purchases or withdrawals. Insurance fraud involves filing false insurance claims to receive undeserved benefits. Online scams use phishing emails or fake websites to deceive individuals into providing sensitive information or sending money.
Theft also comes in multiple forms, such as petty theft, grand theft, burglary, and robbery. Petty theft involves stealing small items of relatively low value, whereas grand theft involves more significant assets. Burglary refers to the illegal entry into premises with the intention of committing theft or another crime, while robbery is the act of stealing from a person directly, often through force or intimidation.
How Fraud is Different from Theft
The key differentiator between fraud and theft lies in the methodology employed. Theft involves the direct physical taking of property, whereas fraud relies on manipulation, deception, or misrepresentation. Furthermore, theft can be more straightforward to detect, as it typically involves visible signs of missing property. On the other hand, fraud can be sophisticated and challenging to identify, often requiring advanced analytical tools and expertise to uncover the patterns and anomalies indicative of fraudulent activities.
Solutions for Fraud and Theft Prevention
Preventing both fraud and theft necessitates a multi-faceted approach combining technology, employee training, and vigilant monitoring. Implementing robust security measures, such as surveillance cameras, access controls, and anti-theft tags, can deter theft. To combat fraud, businesses should invest in AI-powered fraud prevention tools that analyze vast amounts of data to detect abnormal behavior patterns and suspicious transactions in real-time. Regular employee training on fraud awareness and cybersecurity best practices can also enhance the organization’s overall security posture.
Get Comprehensive Protection
Fraud.net offers a cutting-edge AI fraud prevention tool that excels in detecting and preventing both fraud and theft. Its advanced algorithms continuously analyze data from various sources, such as transactions, user behavior, and historical patterns, to identify anomalies and potential fraudulent activities. By leveraging machine learning and artificial intelligence, Fraud.net’s solution adapts and evolves with the ever-changing tactics of fraudsters.
Protect your business from fraud and theft with Fraud.net’s powerful AI fraud prevention tool. Book a demo today to discover how our solution can safeguard your assets, customers, and reputation from malicious actors. Take the proactive step towards comprehensive security and request a demo now!
Fraud Waste and Abuse
Fraud Waste and Abuse is typically a term most commonly used in government and healthcare and refers to several types of negligent and possibly criminal behavior. As defined by United States Code 1347, Fraud is “knowingly and willfully executing, or attempting to execute, a scheme or artifice to defraud any health care benefit program; or to obtain, by means of false or fraudulent pretenses, representations, or promises, any of the money or property owned by, or under the custody or control of, any health care benefit program.” It is illegal to knowingly submit false information in order to receive a monetary or other benefit, the definition of fraud. Waste and abuse, on the other hand, do not require intent and knowledge of wrongdoing. Abuse might take the form of a payment for items or services that have no substantiated basis for payment and/or for which the provider has not knowingly or intentionally tried to get paid. Waste usually refers to the inefficient use of services and is generally not the result of criminal negligence.
Fraud Waste and Abuse Policy
Fraud Waste and Abuse Policy is the set of policies that a business or organization likely have in place so that if fraud or waste occurs within that entity, it has a set of procedures in place to deal with the effects of that fraud or abuse.
Fraud Waste and Abuse Training
Fraud Waste and Abuse Training is training that helps you to understand the definitions of fraud, waste and abuse, identify the principles underlying state and federal laws associated with fraud, waste and abuse, and understand the importance of responsibility for preventing fraud, waste and abuse.
Fraudulent Apps
Fraudulent apps are apps that say they provide some kind of service or entertainment, but their actual purpose is to download malware onto a device, or to discretely attain sensitive information. Some fraudulent apps completely emulate authentic apps, with the intention of tricking people into thinking they are using the real application.
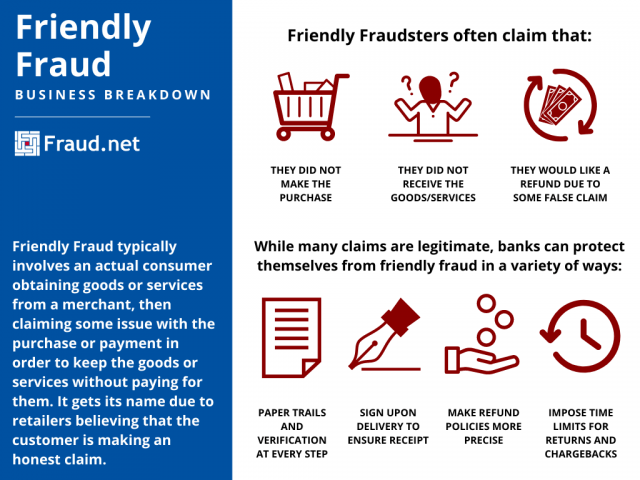
Friendly Fraud
What is Friendly Fraud?
Friendly Fraud, also referred to as first-party fraud, can take many forms, but typically involves an actual consumer obtaining goods or services from a merchant, then claiming they did not make the purchase, did not receive the goods, request a refund from a false claim, or only received a fraction of items, in order to keep the goods or services without paying for them. It gets its name due to retailers believing that the customer is making an honest claim. “Friendly fraudsters” are often good at their crimes, which can sometimes make it hard for customer service to point out a fraudulent claim.
Customers committing friendly fraud make the purchase on a credit card, receive the product or service, and then demand a refund for a lost or short-shipped order, or file a chargeback through their credit card issuing bank, with the intention of receiving a full refund of the purchase amount. Also referred to as chargeback fraud, it is estimated that $4.8 billion was lost by US businesses last year to friendly/chargeback fraud. It is also estimated that as much as 80% of all chargebacks are fraudulent.
How Do You Identify Friendly Fraud?
Identifying friend fraud can be very difficult because of the customer claims that seem believable. Businesses can eliminate the amount of friendly fraud from occurring through tracking and shipping procedures. This could entail that the customer must sign upon delivery, or the business can implement paper trails to prove product orders and delivery. Clear and precise refund policies can also reduce customer fraud claims on falsified product descriptions. Lastly, providing a refund policy that states specific guidelines for the time period the customer has to return a product is critical.
What are the Challenges?
1. Friendly fraud is hard to detect.
Monitoring systems find friendly fraud hard to spot since it’s committed by legitimate customers doing legitimate transactions. Though sometimes the friendly fraud starts as a true claim, what the customer chooses to do ultimately determines the outcome.
In most instances ‘customers’ (real, or disguised fraudsters) are more intentional with their crime; they may claim they didn’t receive items that they did, or they might state that the item received didn’t match the online description, the service provided didn’t meet their expectations, or they don’t remember making the purchase. Each of these instances can be very hard to detect since reports of this nature are often legitimate.
2. Friendly fraud is hard to predict.
Because friendly fraud is usually committed by what appears to be legitimate customers, it’s extremely hard to predict when it will occur. Sometimes, the fraudster may only request a chargeback for a portion of their order, or they may be an ongoing customer who normally doesn’t dispute anything but then chooses to dispute a rare order. It may not even be something they were initially planning or intending to do, but the fraud occurs when they knowingly accept a refund for something they know they should be paying for.
3. Friendly fraudsters wait longer to initiate their chargebacks
The report by Fraud.net found that friendly fraud takes approximately 40% longer for a customer to report than third-party fraud. Third-party fraud is committed by someone who is not the cardholder or the merchant. Examples include identity theft and account hacking. So, a customer who notices a fraudulent charge on their account committed by a third party reports that fraud up to 11 days sooner than when attempting to commit first-party fraud. This time difference can affect the merchant’s anti-fraud attempts, return policies, accounting processes, and more.
4. Businesses are reluctant to flag friendly fraud.
Perhaps the biggest issue that online businesses face is a general unwillingness to mark these returns as fraud. Merchants using rules-based scores typically assign only 17% of the risk to a first-party fraud order as they assign to its third-party equivalent. Merchants blacklist first-party Fraudsters only 15% of the time compared to over 85% in third-party Fraud scenarios. This enables the first-party perpetrators to continue their schemes, often habitually. On average, the first-party fraudsters committed 9 instances of fraud, 3 times more than their third-party counterparts, and are likely still continuing their fraudulent behavior undeterred. Finally, for every chargeback received, merchants issue 7.5 refunds. We estimate that for every first-party Fraud chargeback, there are 2 refunds that are given directly to the fraudster, heading off the necessity for a chargeback. Therefore, the true out-of-pocket cost attributable to first-party fraud is 3 times the recorded cost of ‘friendly' fraud chargebacks.
How Do You Prevent Friendly Fraud?
Because their crimes are hard to recognize, successful friendly fraudsters are often habitual offenders. However, there are some methods you can put in place to minimize risk to your company.
- Participate in a consortium data partnership, where merchants and payment processors share anonymous data about bad actors in their systems.
- Establish a robust first-party fraud monitoring program that includes flagging repeat offenders.
- Incorporate deep learning models to detect the sometimes subtle patterns of first-party fraud
Learn More
- Download: 2020 Friendly Fraud Benchmarking Report
- Listen: Podcast: First-Party Fraud Lowers Profits by 25%
- Read: Top Three Ways to Prevent Friendly Fraud
- Speak with a Fraud Prevention Specialist
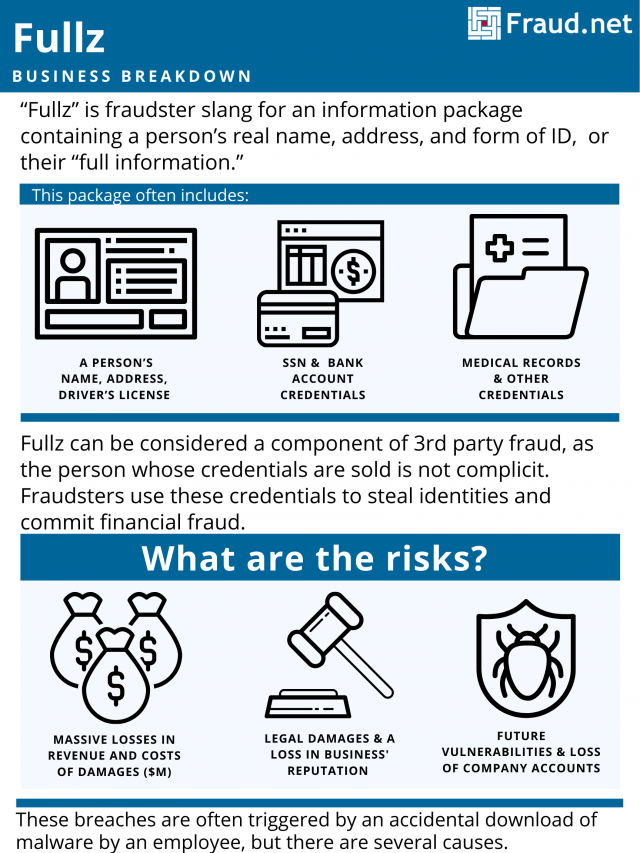
Fullz
What is Fullz?
“Fullz” is fraudster slang for an information package containing a person’s real name, address, and form of ID, or their “full information.” Fullz can be considered a component of 3rd party fraud, as the person whose credentials are sold is not complicit. Fraudsters use these credentials to steal identities and commit financial fraud.
Fullz usually contains a person’s name, address, SSN, driver’s license, bank account credentials, and medical records, among other details. Fraudsters use the victim’s financial reputation for identity theft and fraud, resulting in low credit scores and financial insecurity for the victims. For example, they apply for a loan or credit card with the victim’s good credit. The fraudster applies for the card and uses it, while the victim cannot pay it off and/or attempts to cancel it, harming their credit score.
Fraudsters acquire and sell these information packages through the dark web. They access the dark web using TOR, a system that scrambles users’ virtual trails so they cannot be traced. Identities sell for various prices, depending on the accuracy and viability of the information. Sellers frequently offer discounts for bulk amounts of fullz.
How Are Businesses Affected By Fullz?
Often, fraudsters obtain fullz through corporate and institutional data breaches. Insurance companies, commercial, and financial institutions fall victim due to the sensitivity of the information they possess. These breaches are often triggered by an accidental download of malware by an employee, but there are several causes. Also, businesses and institutions often make themselves vulnerable with poor quality internet security or lack thereof.
As a result, customers find themselves with affected financial reputations and loss of their hard-earned money from account takeovers and cash withdrawal. Businesses face a loss in reputation and if their own financial information is not protected, a loss in revenue. Furthermore, they face legal damages and the cost of damage control for the breach, often in the millions.
How Can You Prevent Fraud?
Businesses and institutions can prevent such breaches with high-quality security solutions to protect purchases and sensitive customer information. With proper web security, institutions avoid the financial and reputational toll of data breaches.
Fraud.net offers a variety of solutions using AI and machine learning to prevent theft of your customer’s information and therefore, your bottom line. We offer dark web monitoring, analytics and reporting, identity protection services, and more.
Contact us for a demo and recommendations for fullz fraud prevention and identity protection.