I2P Anonymous Proxy
The Invisible Internet Project (I2P) anonymous network layer that allows for censorship-resistant, peer to peer communication. Anonymous connections are achieved by encrypting the user's traffic (by using end-to-end encryption), and sending it through a volunteer-run network of roughly 55,000 computers distributed around the world.
Identification (ID)
Identification is the process by which something denotes another object as being a part of a certain category. A human could simply be identified as a human, or could be identified as their role or profession, or by their name; an object could have multiple identifications. In the world of fraud, identificarion is a term brought up often, as people have their identity "stolen", which is when others pretend to be you in for malicious purposes.
Identity and Access Management
Identity and access management (IAM) is a framework for business processes, policies and technologies that facilitates the management of electronic or digital identities. With an IAM framework in place, information technology (IT) managers can control user access to critical information within their organizations.
Identity Fraud
Identity fraud is the situation where a fraudster uses the personal information of a victim, without any approval, to perform a criminal action or to mislead or defraud the other person. Most identity fraud is dedicated to the use of financial benefit, such as access to a credit card, a bank account, or even a victim's loan accounts.
Identity Provider
An identity provider is a federation partner that vouches for the identity of a user. The identity provider authenticates the user and provides an authentication token (that is, information that verifies the authenticity of the user) to the service provider.
Identity Spoofing
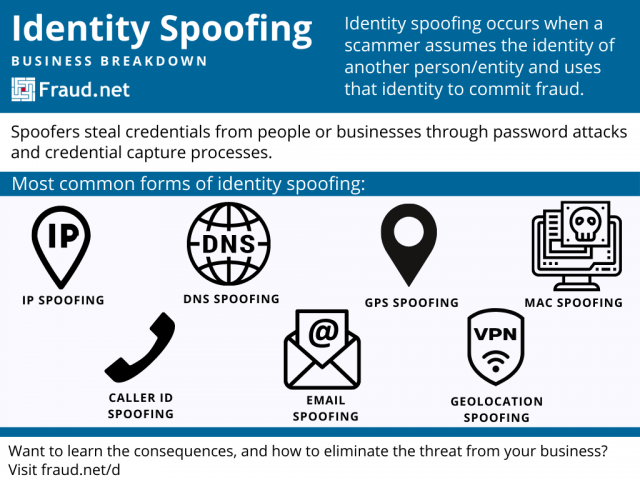
Identity spoofing occurs when a scammer assumes the identity of another person/entity and uses that identity to commit fraud. Spoofers steal credentials from people or businesses through password attacks and credential capture processes.
They use those credentials to facilitate phishing, pharming, identity theft, and business email compromise (BEC) by relying on the trustworthiness of the original identity. Identity spoofing differs from content spoofing, in that the spoofer attempts to "change" the identity of the sender rather than the content being sent. Often these spoofs lead to business email compromise and identity theft, causing organizations millions in losses and/or damages.
Most common forms of identity spoofing
It can be hard to determine whether you face an identity spoofing threat. Users often trust familiar names and addresses despite the possibility that they may be compromised. Familiarize yourself with several forms of spoofing in order to spot them in the future.
ARP Spoofing
ARP spoofing occurs by binding the spoofer’s MAC address (their Media Access Control address) to a legitimate IP address’s default local access network (LAN) gateway. Essentially, a spoofer takes the place of the destination IP and through that spoofing, gains access to their local network. With this access, they capture sensitive information and access unrestricted information on the network. They also manipulate information before it reaches the legitimate IP address. Spoofers then carry out phishing and pharming attacks and assume new identities based on the information they receive. Additionally, ARP spoofers attempt a distributed denial-of-service attack (DDoS) which overwhelms existing security systems by dramatically increasing the number of users it must authenticate.
MAC Spoofing
Each device should have a unique Media Access Control address (MAC) that should not be encountered elsewhere. However, spoofers take advantage of vulnerabilities and imperfections in hardware to spoof the MAC address. As a result, the local network recognizes the MAC address and bypasses certain security protocols. Because spoofers operate with a trusted address, other users fall victim to business email compromise fraud, data breaches, and more. In addition, with trusted access, a spoofed address can deposit malware on a local network. Spoofers then prey on vulnerabilities and steal sensitive information.
IP Spoofing
The source or destination of a virtual message traces back to an IP address associated with a physical location. However, spoofers mask themselves with a legitimate IP address or assume the IP address of someone in that low-risk geolocation. Because many systems do not implement authentication protocols, the masked IP address takes the place of the legitimate source without the legitimate sender or recipient’s knowledge. With this IP spoof, a spoofer can deploy a man-in-the-middle attack within a network, allowing them to steal sensitive information and inform themselves for future fraud attempts. IP spoofing relates to geolocation spoofing:
Geolocation Spoofing
One can spoof their geolocation using a Verified Protected Network (VPN). Some companies offer this direct-to-consumers to protect their information as well as access location-restricted content. Fraudsters use VPNs to place themselves in low-risk locations to avoid their sender information being flagged as an anomaly. Additionally, they use them to mislead security efforts and mask their location to avoid being traced.
Fraudsters also use geolocation spoofing to place themselves in particular states or countries to take advantage of lessened restrictions in the new geolocation. For example, a user in California spoofed their geolocation to play online poker in New Jersey, taking advantage of New Jersey gambling laws. State law in both states prohibits this, so both states located and apprehended the user. The user forfeited about $90,000 in winnings.
DNS Spoofing
Spoofers assume a Domain Name Server (DNS) identity by piggybacking on DNS server caching flaws. As a result, users click on a domain name they trust, but end up on a replica page that leads to phishing or pharming attacks against the user. They click on links within that page and expose themselves to these attacks because they trust the original domain. DNS spoofs, just like many other identity spoofs, often lead to a loss in reputation for the business due to users’ trust being violated by the replica site.
This relates to website spoofing, the use of a replica site in order to steal user information. Spoofers target websites that employees use routinely for their work and construct an almost exact replica. Users click on the link to a trusted website, not knowing that the URL is spoofed. They interact with the website, unknowingly entering sensitive credentials or providing backdoor access to their local network. These spoofs are usually most effective when combined with phishing emails.
Caller ID Spoofing
Spoofers forge caller ID information, presenting false names or numbers and assuming the identity of particular people or organizations. Public networks and Voice over IP (VoIP) networks make this more possible. Callers answer these, believing their legitimacy, and often share credentials or bank account information due to their trust in the legitimate identity. These calls tend to originate in foreign countries where certain protections may not apply to the caller if they find out that they have been scammed.
Email Spoofing
Sender information in the “From” section of an email can be spoofed to hide the origin of fraudulent emails. As long as an email fits the protocols needed by the Simple Mail Transfer Protocol (SMTP) Server, a spoofer easily sends from a falsified email address. The consequences resemble those of IP spoofing and Caller ID spoofing. Spoofers either leverage a man-in-the-middle attack or receive sensitive information, relying on the trustworthiness of the legitimate entity.
GPS Spoofing
Although this is a relatively new form of spoofing, it poses an especially dangerous threat. Identity-based GPS spoofing takes the form of a rebroadcast of a genuine signal, or broadcasting fake signals that very closely represent legitimate signals. A spoofer takes on the identity of the trusted GPS satellites, sending falsified or genuine information with malicious intent.
What Are the Consequences?
The results of a spoofing attack are harmful and detrimental to both compromised identities and those exposed to the spoofer. Several attacks are carried out with various forms of spoofing:
1. Man-in-the-middle attacks
In a man-in-the-middle attack, a spoofer reroutes traditional virtual traffic using a spoofed IP to view the information being sent or manipulate the message on its way to its legitimate destination. Man-in-the-middle attacks are also caused by ARP spoofing and MAC spoofing, both similar to IP spoofing.
2. Phishing
Spoofing often leads to phishing, as it weaponizes the trustworthiness of a recognizable entity. Phishing attacks attempt to capture sensitive information by asking users to click compromised links. Once a user clicks the link, they make themselves vulnerable to back door attacks, where scammers then load malware onto their computer or network to capture more sensitive information.
3. Pharming
Pharming relates to phishing. It often directly results from DNS or Website spoofing. Spoofers send an email from a “trusted” entity and ask a user to click on the link to a website and enter credentials. Those credentials are sensitive data like name, date of birth, address, credit card information, bank information, and more, leading to identity theft and financial reputation destruction.
4. Business Email Compromise
Business email compromise (BEC) directly results from spoofing. Scammers use spoofed email addresses from trusted entities to deceive users into sending money or identity information. They use an organization's name to steal material goods, while the organization gets billed for items they do not receive. Much like other results of spoofing, users trust particular senders and organizations, so they input their information without verifying identity.
Is There a Way to Combat it?
Despite the attack-on-all-fronts that spoofing seems to be, there are ways to mitigate risks. When emails request sensitive information, users should follow up with the sender through another form of communication. Verifying by phone call to make sure that the request is legitimate frequently reveals a compromised identity, saving both the recipient and the spoofing victim.
Another form of protection is multi-factor authentication (MFA), much like the previous method of verifying a request. When entering credentials into an email server or an in-network computer, a user must verify their identity through a separate method. This takes the form of a phone call, text message, email, or push notification to an MFA application.
In addition, you can track how information moves within your network, screen senders based on a set of attributes, and ensure the validity of every source and destination address in your network.
Fraud.net offers a variety of products to combat spoofing, powered by artificial intelligence and machine learning. Even as attacks get more sophisticated, the product evolves with them and learns new ways to combat them.
Contact us for a demo and product recommendations today.
Identity Theft
Identity theft refers to the act of accessing and acquiring elements of another person's identity (i.e. name, date of birth, billing address, etc.) in order to commit identity fraud. Identity theft can take place whether the victim is alive or deceased. Once a person’s identity data is obtained, the data can be monetized by gaining access to their accounts, stealing their resources or obtaining their credit and other benefits. Identity theft (in combination with, and often used interchangeably with, identity fraud) is one of the fastest-growing crimes globally. A criminal can also use stolen identity information to hijack a consumer accounts, commonly referred to as "account takeover".
Improper Disclosures
Improper disclosure refers to when information is mistakenly shown to somebody that has not been authorized by the appropriate people to see it. The term usually relates to medical disclosure, when a persons personal health information is improperly disclosed to somebody.
InfoSec (Information Security)
InfoSec, short for Information Security, refers to the discipline of defending information from unauthorized access, use, disclosure, disruption, modi cation, perusal, inspection, recording or destruction.
Insider Threat
An insider threat can happen when someone close to an organization with authorized access misuses that access to negatively impact the organization’s critical information or systems. This person does not necessarily need to be an employee – third party vendors, contractors, and partners could pose a threat as well.
Instagram scammer
An Instagram scam could be described a scheme fraudsters perform through the use of social media, such as Instagram, or other related applications in the smartphone, in order to gain access to confidential and private information, money or encrypted monetary data with the use of high-level social engineering.
Insurance Fraud
Insurance fraud is any act committed to defraud an insurance process. This occurs when a claimant attempts to obtain some benefit or advantage they are not entitled to, or when an insurer knowingly denies some benefit that is due. There are two types of insurance fraud: hard fraud, which occurs when someone deliberately fakes an accident, injury, theft, arson or other loss to collect money illegally from insurance companies, or soft fraud, in which normally honest people often tell "little white lies" to their insurance company for the purposes of filing or maximizing a claim.
Intellectual Property
Intellectual property, also known as IP, describes an item or idea that has been credited as belonging to somebody in some way. Common types of IPs would be patented or copyrighted materials.
Intelligence
Fraud Intelligence is the leading practical resource for the counter-fraud professional; it provides applied insight, analysis and tools to combat fraud and corruption, whether in the corporate or non-commercial sector, together with coverage of relevant statute and case law.
Intelligence Augmention
Intelligence Augmentation, or IA, is an alternative conceptualization of artificial intelligence that focuses on AI's assistive role, emphasizing the fact that cognitive technology is designed to enhance human intelligence rather than replace it. The choice of the word augmented, which means "to improve," reinforces the role human intelligence plays when using machine learning and deep learning algorithms to discover relationships and solve problems.
Internal Fraud (Insider Fraud)
What is Insider Fraud?
Insider fraud refers to fraudulent activities committed within an organization by individuals with access to sensitive information, systems, or resources due to their positions within the company. These individuals could be employees, contractors, vendors, or anyone with internal access. Insider fraud can involve various illicit activities, such as embezzlement, theft, data breaches, intellectual property theft, and more.
Some statistics related to insider fraud: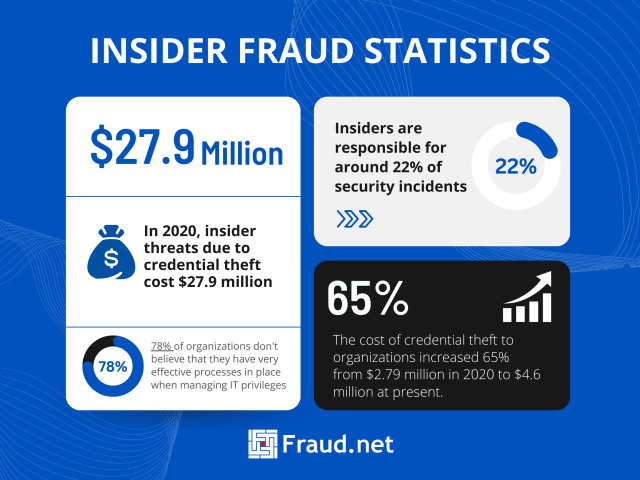
- In 2020, insider threats due to credential theft cost $27.9 million
- The cost of credential theft to organizations increased 65% from $2.79 million in 2020 to $4.6 million in 2022
- Insiders are responsible for around 22% of security incidents
- 78% of organizations don’t believe that they have very effective processes in place when managing IT privileges
Common Types of Insider Fraud
In today’s interconnected digital landscape, various forms of illicit activities have emerged, each targeting valuable assets and personal information. Embezzlement stands as a grave concern, involving the diversion of funds or resources meant for legitimate purposes for one’s personal enrichment. This misappropriation not only undermines the integrity of financial systems but also erodes trust within organizations and communities.
Another prevalent threat is data theft, where individuals or groups unlawfully breach security measures to access and abscond with sensitive information. This stolen data can be exploited for personal gain or even sold on the black market, causing severe financial and reputational damage to the affected individuals or entities.
Moreover, intellectual property theft exacerbates these challenges by undermining innovation and creativity. Unauthorized replication or distribution of proprietary data or trade secrets deprives rightful owners of their hard-earned intellectual assets, hampering progress and hindering healthy competition within industries. Furthermore, identity fraud compounds these issues as stolen identities or credentials are exploited to gain unauthorized access to resources, perpetrate fraudulent schemes, and wreak havoc on individuals’ financial and personal lives.
Insider fraud differs from external fraud in that it involves individuals with some level of trust and access within the organization. External fraud is perpetrated by outside actors with no direct affiliation with the organization. While external fraud often requires bypassing security measures, insider fraud takes advantage of the perpetrator’s legitimate access
Solutions for Insider Fraud
Addressing insider fraud requires a combination of strategies:
- Employee Screening: Thorough background checks and continuous monitoring can identify potential risks during the hiring process and throughout employment.
- Access Controls: Implement strict access controls to limit individuals’ access to sensitive systems and data only to the extent necessary for their roles.
- Regular Auditing: Conduct routine audits of financial and operational activities to detect anomalies or suspicious patterns.
- Whistleblower Programs: Create a safe environment for employees to report suspicious activities without fear of retaliation.
- Security Training: Provide regular training to employees about security best practices, fraud indicators, and the consequences of insider fraud.
- Behavioral Analytics: Utilize advanced analytics to identify unusual behaviors and flag potentially fraudulent activities.
- Clear Policies: Establish clear guidelines for handling sensitive information, conflicts of interest, and acceptable use of company resources.
Fraud.net’s Solution
Fraud.net offers an AI-powered fraud prevention solution that includes specific features to combat insider fraud:
Modern security systems leverage advanced technologies to safeguard against insider fraud and unauthorized data breaches. User Behavior Analysis lies at the core of these systems, diligently observing user actions to swiftly pinpoint deviations from established norms. By discerning unusual behaviors, this approach efficiently detects suspicious insider activities, mitigating potential risks. Complementing this, Anomaly Detection employs cutting-edge machine learning algorithms to meticulously identify atypical patterns and actions that could signify insider fraud. This analytical prowess serves as a formidable defense against emerging threats.
To fortify defenses further, Data Leakage Prevention takes charge of tracking sensitive information’s movement. Through vigilant monitoring, it effectively thwarts unauthorized data transfers, safeguarding against potential breaches. A swift response is key, and the system excels in this aspect with Real-time Alerts. These instantaneous notifications promptly notify relevant parties upon the detection of suspicious activities, enabling immediate intervention. Additionally, Compliance Monitoring plays a vital role, in ensuring adherence to industry regulations and internal protocols. By upholding these standards, it diligently uproots opportunities for insider fraud to take root, fostering a secure environment.
To learn more about how Fraud.net’s AI-driven solution can help safeguard your organization against insider fraud, we invite you to request a demo or book a consultation with our experts. Protect your business from the threats posed by insider fraud today.
Interoperability
Interoperability describes the ability of computer systems or software to exchange and make use of information. Interoperability requires mechanical compatibility among the systems, and it is only able to take results from where profitable contracts have been settled among the systems.
Inventory Fraud
Inventory fraud involves the theft of physical inventory items and the misstatement of inventory records on a company's financial statements. A small business may be a victim of fraud perpetrated by one of its employees, or the business itself may engage in fraudulent activities to trick shareholders and tax agencies. Inventory contains rare materials and uncompleted or completed items that are normally stored in a storage room.
Inventory is one of the biggest assets on a manufacturer’s balance sheet. It’s also one of the hardest assets to measure and track. Therefore, protecting it becomes essential for direct growth. Timely fraud detection and prevention can save your business essential time and money.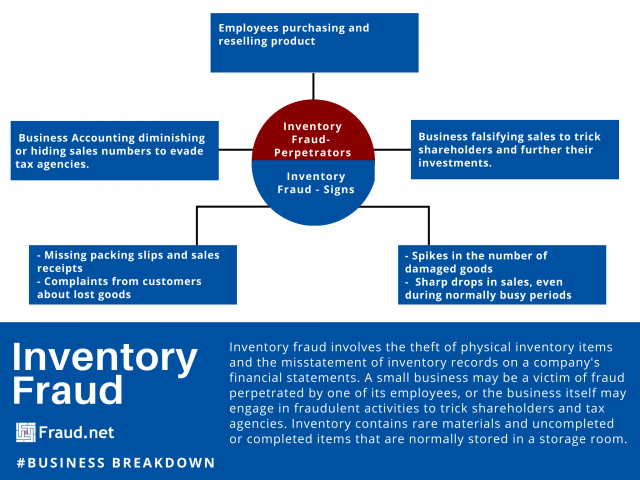
Inventory Fraud: Warning Signs
Telling signs of fraud include missing packing slips and sales receipts, complaints from customers about lost goods, spikes in the number of damaged goods and sharp drops in sales, even during normally busy periods. These events can happen on a digital or physical level. Falsifying orders online, or purchasing orders for resale, is another way company employees might try to benefit.
In a June 2001 article for Journal of Accountancy, Joseph T. Wells, founder and chairman of the Association of Certified Fraud Examiners, wrote about several risk factors for what he called "phantom inventories". To clarify, The term refers to companies who falsify their information to trick tax agencies or shareholders. Attempts to fool company investors may include bogus purchase orders, fabricated shipping and receiving reports, and inflated inventory counts. Fraudsters might even stack empty packing boxes in the company warehouse to feign inventory.
Protect Your Business
To prevent theft in physical warehouses and in offices, make sure to lock storage areas, install video monitoring and alarm systems. Likewise, consider running background checks on employees and conducting physical audits of your inventory at a random interval. As businesses digitize, it's important to have a system in place to assess the risk of customers and their purchases. A system like Fraud.net performs real-time assessments, sometimes hundreds of times per second, of payments, identities, and other data to determine risk even before the point of purchase. Online fraud systems identify and halt anomalous and problematic flare-ups as they happen to help you get in front of potential fraud.
You can prevent inventory fraud by building an environment with the right controls. Learn more about Fraud.net’s end-to-end anti-fraud solution and other tools you can leverage to mitigate threats.
Investment Fraud
Investment fraud is any scheme or deception relating to investments that affect a person or company. Investment fraud includes illegal insider trading, fraudulent stock manipulation, prime bank investment schemes and hundreds of other types of financial scams.
Invisible Web
The Invisible Web is the part of the World Wide Web, which is not indexable by search engines and is therefore invisible. In contrast to the Surface Web, the Invisible Web consists of data and information that cannot be searched with search engines for various reasons.
IOD - Impersonation of the Deceased fraud
What is Impersonation of the Deceased Fraud?
Impersonation of the deceased fraud, also known as ghosting, is a type of identity theft that occurs when someone uses the personal information of a deceased person to commit fraud. This can include opening new credit accounts, applying for loans, or making other financial transactions in the deceased person’s name. Sometimes, the identity thief may even try to assume the deceased person’s identity by obtaining a new driver’s license or passport in their name.
Here are some more recent statistics related to Impersonation of the Deceased Fraud:-
- Nearly 2.5 million dead people are victims of identity theft every year, according to a data analysis by fraud prevention firm ID Analytics.
- Fraudsters intentionally use the identities of the deceased at the rate of more than 2,000 per day.
- The number of consumer identity theft complaints rose 3.3%, to just over 1.43 million.
- In 2022, there were over 1.1 million reports of identity theft received through the FTC’s IdentityTheft.gov website.
- There is an identity theft case Every 22 seconds.
- ID theft comprised about 24% of the 5,883,409 reports of fraud, identity theft, and other complaints.
Common Types of Impersonation of the Deceased Fraud
- Obtaining credit cards or loans in the deceased person’s name
- Using the deceased person’s identity to apply for government benefits
- Filing a tax return in the deceased person’s name to obtain a refund
- Selling the deceased person’s personal information on the dark web
Solutions for Impersonation of the Deceased Fraud
Preventing impersonation of the deceased fraud requires a multi-faceted approach. One solution is to secure the deceased person’s personal information by shredding important documents that contain their personal information. Additionally, family members should notify financial institutions, credit bureaus, and government agencies of the death to prevent fraudulent activities.
Fraud.net Helps You Mitigate Identity Theft
Fraud.net offers a comprehensive fraud prevention solution that includes impersonation of the deceased fraud detection capabilities. Their AI-powered platform can analyze large amounts of data in real-time to detect and prevent fraudulent activities, including impersonation of the deceased fraud.
Fraud.net’s Collective Intelligence Network enables them to reinforce identity verification processes, cross-referencing identity elements with databases of deceased individuals. This proactive measure enhances fraud prevention by preventing the misuse of identities linked to the deceased, reflecting their commitment to robust security and compliance.
To learn more about Fraud.net’s impersonation of the deceased fraud prevention solution, you can book a demo on our website.
IoT Botnet
Also known as a zombie army, a botnet is a collection of internet-connected devices that an attacker has compromised. These botnets can try to infect more computers or spread spam for affiliate fraud, amongst other reasons. They can also act as a proxy to mask a criminal’s original IP address. Botnets mainly act as a force multiplier for individual attackers, cyber-criminal groups and nation-states looking to disrupt or break into their targets’ systems. Commonly used in distributed denial of service (DDoS) attacks, botnets can also take advantage of their collective computing power to send large volumes of spam, steal credentials at scale, or spy on people and organizations.
IP Address
An Internet Protocol address (IP address) is a rational numeric address that is assigned to each computer, printer, or some other device that is considered to be a part of a TCP/IP-based network. An IP address is the main element on which the network structure design is built, and there is no network that could ever exist without any IP address.
IP Address Verification
Internet Protocol or IP Address Verification could be defined as a set of processes and procedures that ensure that everything you produce, buy, or sell on the Internet will have a legal and registered IP address.
ISP Monitoring
ISP monitoring is the practice through which ISPs record information about your online connections and activities. That means that everything from your search history to your email conversations are monitored and logged by your Internet service provider.
Issuer (Issuing Bank)
The Issuing Bank is the financial institution which issues individuals with credit cards or debit cards and extends short-term lines of credit to purchase goods and services. Familiar issues include Bank of America, Wells Fargo, Citibank and The issuer settles card transactions for the purchaser or card holder whereas its counterpart the acquiring bank or merchant acquirer, is the bank that is responsible for settling credit and debit card transactions on behalf of the merchant. Issuers generally manage the credit and debit card programs on behalf of the card networks, such as Visa and Mastercard, and for their role in the card payment process, receive the majority of the interchange and other fees in a credit card and debit card transaction. Discover and American Express are both issuers and card networks.