Ransomware
Malware that blackmails the user in order to have the program be removed. It is a virus that blocks access to a computer via encryption, unless a certain sum is paid (generally through cryptocurrencies to maintain anonymity). The criminals usually threaten to delete important files, or disable the entire computer if the money isn’t paid by a certain deadline.
Real-Time Risk Management
Real-time risk management is a process which enables a person to handle risks associated with payments as the payment happens. It allows the person to effectively ensure that all the transactions are being carried out in a proper way, and can be denied at the business owner's discretion in case they believe a purchase to be fraudulent. This solution can be provided by a third-party as well.
Record Destruction
Record destruction refers to the process of illegally destroying information stored in the form of documents. This is an ethically wrong practice and if spotted within an organization can lead to the termination of that person's employment.
Relying Party
Relying party or third party is a computer term used to refer to a server providing access to a secure software application. Claims-based applications, where a claim is a statement an entity makes about itself in order to establish access, are also called relying party (RP) applications. Actually RP refers to the person who provides services to the customer not directly but just by connecting the customer to the actual seller. Usually, the host or the merchant has to identify the real party that is delivering services to the customers.
Reshipping Fraud Scheme
In a reshipping scam, the criminals purchase high-value products with stolen credit cards and recruit willing or unsuspecting people (reshipping mules) to receive and forward the packages on behalf of the criminals. In the package, there will be stolen items and in case of arresting, the re-sender will be arrested first.
Retail Loss Prevention
Retail loss prevention is actually a set of practices and methods which are employed by retail companies to preserve profit, so to ensure that there are as few scams associated with transactions as possible. Profit preservation is any business activity specifically designed to reduce preventable losses. Usually, most crimes are related to retail and in order to minimize this risk, these practices are adopted by the retailer, and are known as retail loss prevention methods.
Return Fraud
What is Return Fraud?
Return fraud is an online scam that occurs when a person purchases an item from a retail store with the intent to return it immediately or use duplicate receipts to get money back. It is the act of defrauding a retail store via the return process. Fraudsters commit this crime in various ways. For example, the offender may return stolen merchandise to secure cash, steal receipts or receipt tape to enable a falsified return, or use somebody else's receipt to try to return an item picked up from a store shelf.
There are several types of return fraud, including:
- Returning stolen merchandise - shoplifting and returning merchandise for a refund of the full price.
- Receipt fraud - stealing or falsifying receipts to return merchandise for profit. Another version of this is purchasing goods at a low price from one store and returning at another with a higher price to profit off the difference.
- Employee fraud - assistance from employees to return stolen goods for full price. This is a form of insider fraud.
- Price switching - placing higher price labels on merchandise to later return them at a higher price than the initial purchase. This is similar to profiting off the price difference in receipt fraud.
- Price arbitrage - purchasing similar-looking but differently priced goods, and returning the cheaper item as the expensive on and profiting off the difference.
- Switch fraud - purchasing a working item, and returning a damaged or defective item that was owned before the purchase of the working item.
- Bricking - purchasing a working electronic item, and stripping it of all valuable and necessary components to make it unusable, then returning it for profit.
- Cross-retail return - returning or exchanging an item purchased at another retailer for cash, store credit, or a similar, higher-priced item at another retailer.
- Open-box fraud - purchasing an item from the store and returning it opened with the intent to repurchase at a lower price under “open-box” store policies. This is similar to price-switching.
- Wardrobing - purchasing merchandise for short-term use with the intent to return the item (ex. purchasing a dress, wearing it for a night with the tags still on, and returning it).
The Cost of Return Fraud
The retail industry loses about $24 billion annually in return fraud and policy abuse, accounting for 8% of returns. In 2020, of the 10% of returned transactions, 6% were fraudulent, leading to a loss of $25.3 billion for retailers. As retail shifts online, 38% of merchants see an increase in buy online, return in-store purchases, and 29% of merchants report an increase in fraudulent returns among such transactions. Furthermore, 21% of returns made without a receipt are fraudulent. As a result, merchants often raise prices to offset losses, unfortunately affecting customer experience.
Holiday Shopping Seasons Increase the Risk
25% of annual product returns occur between Thanksgiving and New Years Day and return fraud increases during this time as well. According to the National Retail Federation, a quarter of holiday shoppers buy items with the intent of returning them later. This leads to merchants preparing for a large volume of returns. In 2018’s holiday season, about 10% of returns were expected to be fraudulent, leading to a loss of $6.5 billion in holiday return fraud. Due to high customer volume, sometimes loss and fraud prevention measures become more relaxed despite the increased vulnerability.
As a result of increased purchase and return volume, retail staff becomes overwhelmed with handling returns as well as investigating fraudulent ones. Often this leads to more staff being hired over the holiday season, increasing the merchant’s operating costs. If they choose not to or cannot hire more staff, the existing staff becomes overworked trying to keep up with the increased volume.
How to Prevent Return Fraud
Returns are necessary for retail to promote customer loyalty and satisfaction. Unfortunately, this poses a challenge for combatting return fraud. Policies must be clear and restrictive enough to effectively prevent return fraud, but flexible to avoid discouraging legitimate returns and exchanges. They also should be easy to access on online shopping sites and packaging/receipts for shipped goods.
In addition, as much data as possible must be collected from fraudulent returns to prevent repeat offenses and inform fraud prevention for future threats. Collective intelligence informed by transaction data helps fight future fraud by arming prevention and detection services.
Fight Return Fraud with Fraud.net
Fraud.net has a large suite of solutions helpful in fighting return fraud, among other types of fraud. With identity verification, dark web monitoring, and datamining services, fighting return fraud becomes easier and more efficient.
Contact us today for a free demo and recommendations to help you protect your profits from return fraud.
Return On Investment (ROI)
Return on investment (ROI) is a performance measure used to evaluate the efficiency of an investment or compare the efficiency of a number of different investments. ROI tries to directly measure the amount of return on a particular investment, relative to the investment’s cost.
Risk Assessment
Risk assessment is the systematic process of evaluating the potential risks that may be involved in a projected activity or undertaking. To assess the risks, different tools and methods can be utilized. In addition, risk assessment also involves determining the likelihood of risks that will threat the system in the future.
Risk Management
Risk management describes the process and practices of companies in attempting to prevent malicious or fraudulent activity from occurring within their systems, as well as addressing any other issues that would create financial risks. It can be more simply defined as the practice of forecasting and evaluating potential financial risks alongside identification procedures that aim to avoid or minimize their impact.
Risk-Based Authentication (RBA)
What is risk-based authentication?
Risk-based authentication (RBA) is a non-static authentication system that takes into account the profile (IP address, User-Agent HTTP header, time of access, and so on) of the agent requesting access to the system to determine the risk profile associated with that transaction. This type of authentication method is used to determine high-risk security threats to protect sensitive information. When the risk level increases, authentication becomes more extensive. False insurance claims are insurance claims filed with an intent to defraud an insurance provider.
A common example of risk-based authentication is when a user accesses their bank account outside of their home state or country. Because the user's geographic location is different, the indication of potential risk is alerted. The user will then proceed to answer their security questions in order to access their bank account information.
User and Transaction Dependent Authentication
Risk-based authentication can be user-dependent or transaction-dependent. A user-dependent authentication means that the authentication process will look the same for the user, every time. This means that a user can expect to input the same credentials when authentication is prompted during a login attempt. A transaction-dependent authentication means the user could have to input different credentials if authentication is promoted, even after inputting a username and password. Instead of answering the same security questions, they may have to answer other credentials such as their social security number, date of birth, etc. to gain access to their account.
Fraud.net and Fraud Prevention
Fraud.net offers a variety of services to help prevent fraud through identity verification and risk-based authentication, among other methods. With our software and service suite powered by machine learning and artificial intelligence, organizations can spend less time doing detection and more doing analysis - saving money, time, and profits.
To learn more about the services Fraud.net offers, contact us for a demo and security recommendations today.
Romance Scams - How To Avoid Losing Millions To One
How to Avoid Losing Money to a Romance Scammer
Millions of people fall victim to romance scams, or fraudsters portraying themselves as potential romantic partners only to trick their mark into sending them their money. Scammers create fake profiles on dating sites or social media and strike up a conversation to build trust. Then, they make up a story and ask for money or threaten the victim with blackmail.
They may request money for plane tickets to meet the victim, or pay for medical or legal expenses or a visa. On the other hand, they may threaten the victim with messages about compromising photos, or sharing sensitive information with friends and family on social media and offer to stand down in exchange for payment.
Scammers request this money to be wired through payment services or through reload or gift cards for vendors like Amazon, and often, the victim believes the ruse and pays the amount. Unfortunately, once they realize the scam, these transactions are usually impossible to reverse or track, and the victim loses hundreds of dollars. The payment company or the gift card issuer now shoulders the burden.
The Cost of Romance Scams
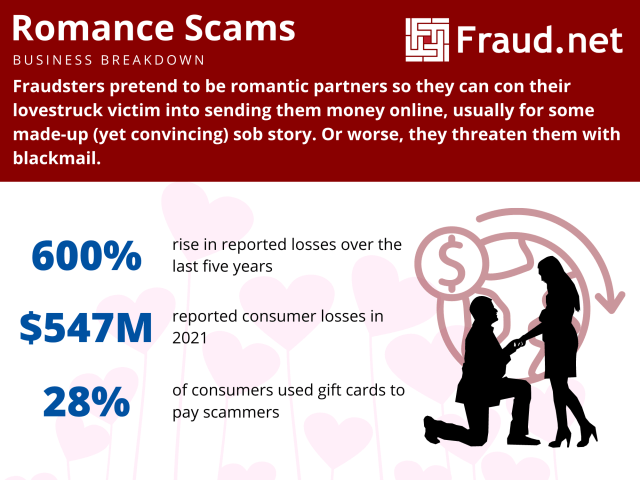
These scams cost consumers upwards of $304 million in 2020 and have risen to a record $547 million in 2021, and reported losses increased by 600% from $87 million in 2017. In the last five years, the cost of romance scams increased to $1.3 billion, more than any other type of fraud.
The most profitable avenue for fraudsters to conduct romance scams is social media, with consumers reporting losses of $770 million in social media fraud schemes. The top platforms for conducting these scams were Facebook and Instagram.
Furthermore, the largest reported losses were paid in cryptocurrency, reaching a staggering $139 million in the last year alone, 25 times the numbers reported in 2019. Gift cards were the most prominent payment method for these scams, with 28% of people reporting the use of these. Losses with this method amounted to $36 million last year.
This rise could be attributed to the increased digital presence and lack of face-to-face interaction due to the pandemic. However, presence on dating apps and sites increased outside of the pandemic as well.
What do Romance Scams Have to Do With My Business?
These scams are essential for businesses to note as they are a remittance issue that affects merchants, payment companies, and platforms.
Once the scammer obtains wired funds, the onus of the loss now falls on the transfer service platform, the merchant who hosts that transfer service (or sells the gift cards), or the payment service provider who hosts the victim’s payment account or issues their card. So, this issue results in increased chargebacks and disputes, and companies must screen these on top of their usual burden for fraudulent chargebacks.
Additionally, romance scams can manifest as an email fraud issue, as victims may fall prey to phishing emails. Or, the fraudster may ask them to enter credentials on a spoofed or dangerous site. Romance scams could also manifest as an insider fraud issue through blackmailing the victim into committing cybercrime in exchange for withholding sensitive photos or information from social media sites.
Combat Romance Scams with AI
The best way to combat the effects of romance scams is to employ a strong fraud defense, with comprehensive risk detection and analysis. Flagging suspicious activity, employing verification tools for identities and transactions, and monitoring chargebacks will ultimately save both you and your customers from romance scammers.
With our award-winning AI-powered risk management ecosystem, run checks for suspicious transactions quickly and accurately. Screen for inconsistencies within accounts, verify recipients against billions of data points, and bolster your fraud protection to give both you and your customer peace of mind.
To discover how Fraud.net can help you combat payment or remittance fraud, email fraud, or provide award-winning insider threat detection… schedule a free demo of how our fraud-prevention software can accurately flag fraudsters on autopilot.
Read our related content:
Rules Engine
A rules engine is a software system or a program that is capable of executing one or more than one business rules in an environment of run time production. The rules might be coming from a company policy, legal regulation, or some other sources. Most organizations tend to them.
Rules-Based Fraud Detection
Rules-based fraud detection identifies fraud based on a set of unusual attributes, including unusual time stamps, account numbers, transaction types, and amounts, among other criteria.
How Rules-Based Fraud Detection Works
This methodology of fraud detection operates on a set of "rules", or a set of conditions that when detected, signify potentially fraudulent transactions.
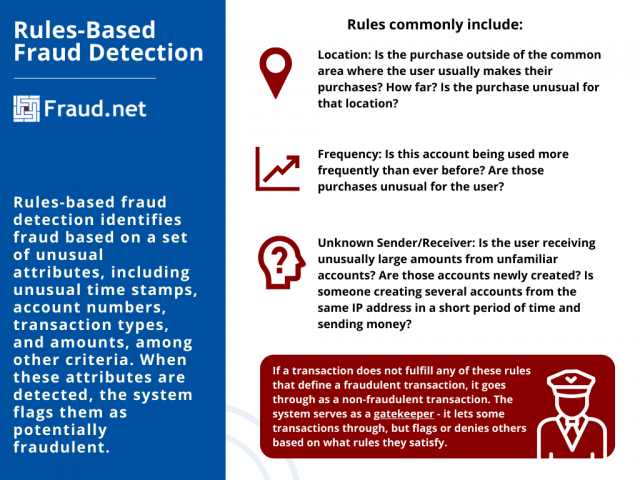
Rules commonly include:
- Location - if a transaction occurs outside of the usual location of the user. For example, if a user whose purchases commonly occur in Santa Fe suddenly has a transaction appear in rural Ohio, or Eastern Europe.
- Frequency - If a user rarely uses an account that suddenly lights up with transaction activity. Further, if an account number is used in a variety of transactions with little to no connection, or if there is an unusually high amount of small transactions for the user.
- Sender/Receiver - If a user receives payments in large amounts from multiple newly created accounts. On the other hand, if someone from the same IP address is creating multiple credit card accounts in a short period of time and sending money.
The Gatekeeper
If a transaction does not fulfill any of these rules that define a fraudulent transaction, it goes through as a non-fraudulent transaction. The system serves as a gatekeeper - it lets some transactions through, but flags or denies others based on what rules they satisfy. Unfortunately, this gatekeeper fails sometimes, with false positives and negatives.
Strengths and Vulnerabilities
Rules-based systems effectively detect fraud based on a set of rules, cutting human intervention down, therefore lowering overhead security costs for businesses. Despite this, there are some weak spots that rules-based systems could address.
Vulnerabilities
-
Blind Spots
These systems contain blind spots, areas which rules do not cover. In these situations, fraudsters spoof transactions or circumvent existing rules. Traditional systems rely on rules set by human security officers, and must manually be updated in response to threats. Between the updates, fraudsters take advantage of blind spots.
-
Lack of Data
Rules-based systems work best with a large aggregation of data, to better address all vulnerabilities that institutions face. If an institution is limited to a small data pool, it cannot accurately and effectively identify fraudulent transactions. This is also true in machine-learning systems.
-
Incorrect Data
A rules-based system works best when the human security officer sets useful and effective rules. Incorrect or badly defined rules lead to lower fraud detection and false positives.
Strengths
-
It Works Quickly
The benefit of rules-based systems is their low complexity. They scan through all transactions and identify fraud based on rules, allowing for more transactions to be screened quickly. This, combined with machine-learning systems for more sophisticated attempts, provides great security for transactions.
-
Transparency
Because rules-based systems operate based on what rules are satisfied, they are easy to interpret, or "transparent". If an issue arises in reporting, such as a false positive or negative, human intervention can quickly identify and correct it.
-
Simplicity
In some cases, keeping it simple is actually better - this holds for rules-based system implementation. Rules-based fraud detection systems are easy to develop and validate, and they work rather quickly in operation. While rules-based systems are not necessarily a "set it and forget it" solution, their simplicity offers quick and easy implementation.
Rules-Based Fraud Detection and Machine Learning
Algorithmic fraud detection, better known as machine-learning-based fraud detection, operates similarly to rules-based fraud detection. However, instead of relying on human intervention to quality check and update rules as it gathers more information, these systems do this work automatically. Algorithmic systems change their rules and responses based on both past and emerging threats. The human intervention occurs mostly at the data input stage and the quality assurance stage at the end of the process. In any case, algorithmic models cut the necessity for human intervention down significantly, saving institutions money in overhead and labor.
Rules-Based Fraud Detection and Protection with Fraud.net
Fraud.net has a large suite of products that operate using a combination of rules-based processes, artificial intelligence, and machine learning. These products offer top-of-the-line security against fraud attempts, and self-regulate based on both your and your consumers' transaction behavior.
Learn More
-
Rules & Workflows - Flexible, Customizable, and Powerful
-
Video: Fraud.net Rules and Analytics
-
Speak with a Fraud Prevention Specialist
Run of network (RON)
Run of Network, or RON, is actually a form of internet marketing where an online advertising campaign is applied to a wide collection of websites without the ability to choose specific sites. In run-of-network advertising, advertisers generally give up say over placement in return for low rates and broad reach. Ads may be placed randomly in unsold, less valuable portions of sites within an ad network.